This article is the second in a series which covers Polycom’s RealConnect service, a Microsoft Azure-based video interoperability service for Skype for Business and Microsoft Teams meetings.
RealConnect Service for Skype and Teams – introduces the overall solution and the steps to activate the service for use with Skype for Business Online meetings and/or Teams meetings. (A future article will cover the additional configuration steps required to support Skype for Business Server or Hybrid deployments with the service.)
Polycom One Touch Dial Service – explains what this ancillary service is, how it works, and provides detailed configuration steps for using it with Polycom VTCs. (A future article will cover the configuration for Cisco VTCs.)
Polycom Cloud Relay – outlines the purpose of this component, how it works, and then walks through the steps for deploying a Cloud Relay virtual server on-premises. This on-premises server is an optional component to the RealConnect service, only needing to be deployed when using Skype for Business Server and/or supporting Cisco endpoints with the One Touch Dial service.
The specific term “One Touch Dial” (or its initialism “OTD”) is not new. It has been used for several years to describe various concepts throughout Polycom solutions: a workflow, an action, a server, an application, and now a service. To offer some clarity, OTD started as an application which provided a simple meeting joining experience to Polycom and Cisco VTCs for on-premises RealConnect meetings. This application is one of several custom applications which runs on an a dedicated on-premises server called the Polycom Workflow Server. This server is used only with the traditional RealConnect deployment model which utilizes on-premises Polycom MCUs.
More recently the OTD functionality was put into Microsoft Azure for use with the RealConnect service. Yet, not 100% of what OTD does can be put into the cloud. The on-premises version of OTD essentially operates as both a Microsoft Exchange Web Services (EWS) proxy and an emulator of the Cisco Telepresence Management Suite (TMS), at a Calendaring level only. Each of those roles are needed to support both Polycom and Cisco endpoints. Polycom endpoints (like the Group Series, HDX, Trio, etc) all operate as native EWS clients and will automatically retrieve meeting invitations by routinely polling the appropriate Exchange Server or Exchange Online, which is essentially a ‘pull’ operation. So regardless of the location of the endpoint it is easy for these devices to open a new connection to a server over HTTPS 443.
On the other hand, Cisco endpoints that natively support One Button To Push (OBTP) do not operate using the same approach. These endpoints are effectively dumb and rely on another server (TMS) to retrieve meeting invitation emails on their behalf, which are then relayed to the endpoint. Given that this ‘push’ operation can not typically be performed from an Internet-based service down to a host sitting on a private network behind firewalls then the relay would need to also exist within the same routed internal network. Thus, the Polycom Cloud Relay is utilized as this relay. Meaning that while most of the operation of the original OTD application was placed into Azure as a service, the TMS emulator portion is provided as an applet which resides on the on-premises Cloud Relay virtual server.
Workflow Explained
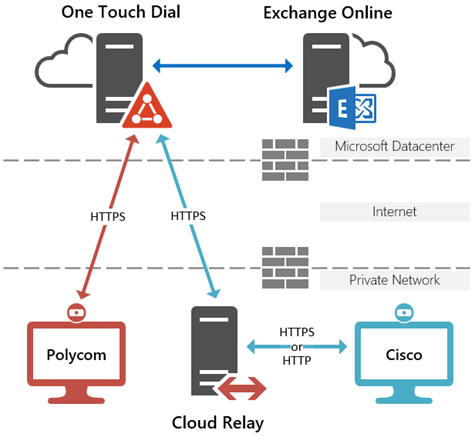
This simple diagram depicts how the OTD service works for both types of supported endpoints.
The OTD service acts as an EWS proxy and will fetch the mailbox contents on behalf of the endpoint. This middle-man step is required as OTD’s primary function is to scan the invitation, looking for RealConnect-enabled meeting invitations. When an applicable Skype for Business or Teams meeting invitation is found then it reformats the outgoing copy to match what the associated endpoint expects to see to enable the ‘Join’ button to appear and operate correctly on the endpoint. As the required formatting is different between Polycom and Cisco endpoints then OTD will handle this accordingly.
- Polycom VTCs communicate directly with the OTD service currently hosted in Microsoft Azure, so when the endpoint performs a routine mailbox check it will connect to the OTD service to trigger the process. OTD processes the messages and then passes it on to the Polycom endpoint. To the endpoint this process is transparent and looks like a regular EWS message exchange.
- Cisco VTCs do not initiate this process though; the environment configuration drives this. The OTD service itself will monitor mailboxes associated with Cisco endpoints and routinely check for new messages. If any are found then it will push the message down to the Cloud Relay (which has previously established an ongoing secure two-way connection to the OTD service) and then the Cloud Relay will act as a TMS Calendaring service and relay the message to the target Cisco VTC over the local network. The connection from the relay to the VTC is first attempted securely via HTTPS, but if connectivity over TCP 443 is not available then it will failback to attempting to connect via HTTP over TCP 80.
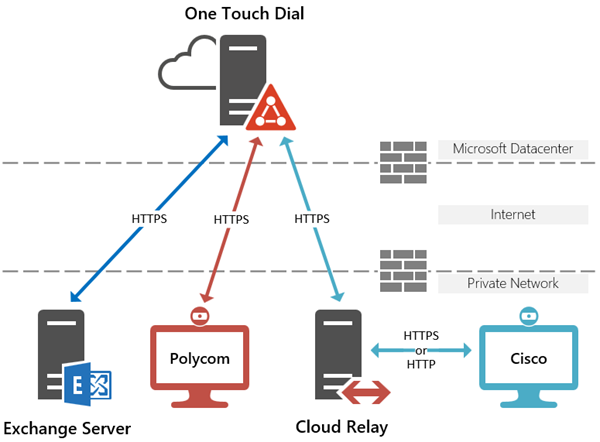
Note that while the diagram above depicts Exchange Online as the mailbox location the OTD service also supports on-premises Exchange Server environments. As long as Exchange Web Services has been published externally in a deployment then the service can leverage the external EWS FQDN to connect to the server and access the required mailboxes.
Thus the OTD service can be used with Exchange Server, Hybrid, or Online topologies. For the articles in this series a standard Microsoft Office 365 tenant is being used so Exchange Online mailboxes will be leveraged for all configuration steps.
Overview
There are several different configuration options available to provide One Touch Dial capabilities to Skype for Business Server, Online, and Teams meetings which are enabled for RealConnect. Polycom endpoints support multiple options, but to support Cisco endpoints there is only one possible configuration.
Pass-Through Authentication
Polycom endpoints can by default simply leverage pass-through authentication via the OTD service to access the requested mailbox in Exchange. The required credentials are stored on the endpoint and are used to authenticate through the OTD service (as a proxy) into Exchange. Pass-through authentication can be used with the actual mailbox account’s credentials or a shared service account if desired.
This method of using the mailbox’s own credentials on the endpoint configuration is the easiest and requires no configuration in the OTD portal, but it may not be possible in environments where resource mailboxes are disabled in Active Directory. An alternative approach is to utilize a service account to authenticate to Exchange in the event that the resource mailboxes themselves are not enabled for authentication, which is common (and the default) behavior for Exchange resource mailboxes. The service account model can be configured to use either pass-through or proxy authentication models.
- With pass-through authentication a single service account is created and then delegated permissions to all applicable resource mailboxes. The service account credentials are entered in each endpoint alongside the SMTP address of the desired resource mailbox for a given endpoint. The same service credentials are used on every endpoint for accessing each unique resource mailbox.
Proxy Authentication
The OTD service must first be configured to leverage this model as a service account is used alongside manual endpoint configuration in the portal. To provide One Touch Dial to any supported Cisco endpoints this option is required; pass-through authentication is not applicable. Polycom endpoints can also use this option if the credentials of the service account are to be known and managed only by IT staff with access to the OTD portal while a different set of local credentials which are known by support staff will be used on the endpoints themselves. This is a less common approach but does offer flexibility in larger deployments with separate teams managing different components of the overall solution.
- For proxy authentication the same service account is created and then delegated permissions to all applicable resource mailboxes but is instead stored directly in the OTD portal configuration. Then unique credentials are manually generated in the OTD portal for each newly configured device, to be used for that endpoint’s local configuration. The OTD service will act as an authentication proxy, using the local set of credentials for connections from endpoint to the OTD service, and the service account for all communications between itself and Exchange.
This remainder of this article covers the multiple configuration options available to Polycom VTCs. A separate article outlines the configuration for Cisco VTCs which require additional steps and as well as the deployment of a Cloud Relay server on-premises.
There are two general configuration models available for One Touch Dial:
- The first is a standard configuration which leverages autodiscovery to locate resource mailboxes stored in Exchange Online that have been correctly configured to allow authentication using their own credentials. This approach does not require any configuration on the One Touch Dial portal. As stated, this model only works with Exchange Online mailboxes. For Exchange Hybrid environments as long as the VTC’s mailbox is stored in Exchange Online this configuration can be used.
- The second, more complex configuration option is required when accessing room mailboxes stored on an Exchange Server as a service account will be required alongside configuration of the One Touch Dial portal to connect to the external Exchange Web Services using that service account. This model is also required when using the proxy authentication model with Exchange Online mailboxes.
Standard Configuration
This section will walk through creating or validating the required Exchange mailbox and then configuring a single Polycom Group Series endpoint to leverage the OTD service. For this method to be viable the resource mailbox (new or existing) will need to be hosted in Exchange Online and enabled for authentication. If that is not possible or not allowed by enterprise policies then skip to the next section covering the Service Account Configuration methods.
As explained earlier, there is no need to first sign in to the One Touch Dial portal and perform any service configuration steps when using Polycom endpoints. The service will automatically leverage Exchange Autodiscover to locate the source mailbox in Exchange Online.
Prepare PowerShell
The following environment preparation steps are performed using Windows PowerShell to connect to multiple online modules. The workstation used to perform these commands may need to have some initial setup steps performed to access these modules. Only the Exchange Online PowerShell and MSOnline modules needs to be installed to support the cmdlets in this article.
- Follow the steps in the Managing Office 365 with PowerShell article and then connect to both Exchange Online and the MSOnline modules as instructed. (There is no need to connect to the AzureAD or Skype for Business modules.)
Create Mailbox
This step may not be required as typically a mailbox already exists for a conferencing room space that is represented in Outlook to book as a resource. If a new mailbox needs to be created for a specific VTC then the following steps can be used to create an Exchange Room Mailbox using PowerShell.
For this article a new resource mailbox will be created for use with a single Polycom Group Series endpoint.
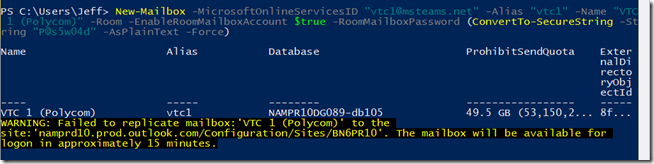
- Run the following New-Mailbox command to create a new resource mailbox of Room type, updating the red text with the desired unique ID, Alias, Name, and Password.
New-Mailbox -MicrosoftOnlineServicesID “vtc1@msteams.net” -Alias “vtc1” -Name “VTC 1 (Polycom)” -Room -EnableRoomMailboxAccount $true -RoomMailboxPassword (ConvertTo-SecureString -String “P@s5w04d” -AsPlainText -Force)
If a replication failure warning appears it can safely be ignored as it is just reporting that the new mailbox will take some time to be created and replicated within Exchange Online. The following configuration steps can be performed immediately.
If needed, repeat this process to create a room mailbox for every Polycom endpoint which will be used with OTD service.
Configure Mailbox
Using either the new mailbox created above or an existing mailbox the following commands will ensure that the mailbox is correctly configured. Depending on how existing resource mailboxes were created these parameters may already be set correctly, but sometimes the existing settings will purge the meeting invitation contents to save on mailbox storage. Without that data included in the room’s copy of the invite then OTD has no information to process and then no ‘Join’ button would appear on the invited VTC.
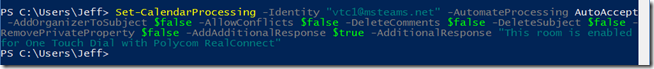
- Run the following Set-CalendarProcessing command against the new mailbox as identified by the Identity parameter. Leave all other parameters at the documented vales, aside from the -AdditionalResponse setting which can be customized to include any message.
Set-CalendarProcessing -Identity “vtc1@msteams.net” -AutomateProcessing AutoAccept -AddOrganizerToSubject $false -AllowConflicts $false -DeleteComments $false -DeleteSubject $false -RemovePrivateProperty $false -AddAdditionalResponse $true -AdditionalResponse “This room is enabled for One Touch Dial with Polycom RealConnect”
If needed, repeat this process for every room mailbox (new or existing) that is (or will be) associated with a supported VTC to leverage OTD.
Configure Endpoint
The following steps are used to perform the calendar setup directly on the Polycom Group Series with the newly created and configured resource mailbox.
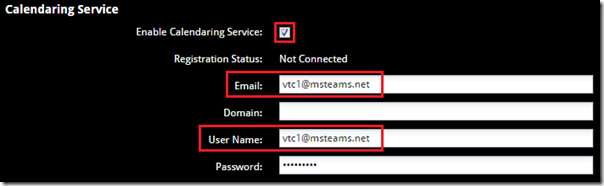
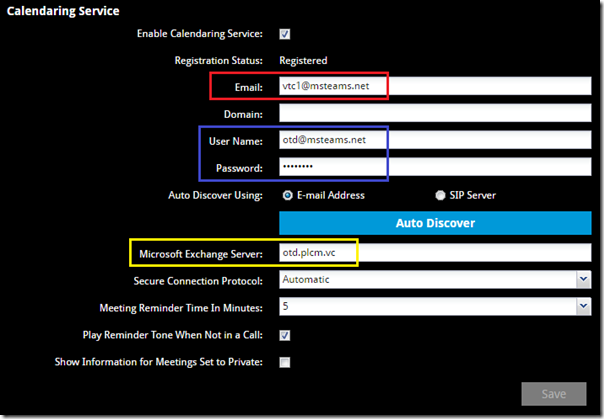
- Connect to the web management interface on the Group Series endpoint and then navigate to the Admin Settings > Calendaring Service menu.
- If not already enabled click the checkbox next to Enable Calendar Service.
- Enter the Email address (e.g. vtc1@msteams.net), User Name (e.g. vtc1@msteams.net), and Password for the desired resource mailbox. (Leave the Domain field blank as the User Principal Name format is used in the User Name field which already includes the domain name.)
-
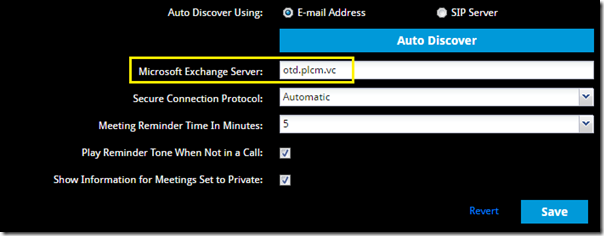
In the Microsoft Exchange Server field enter the Polycom One Touch Dial service FQDN of otd.plcm.vc and then click Save.
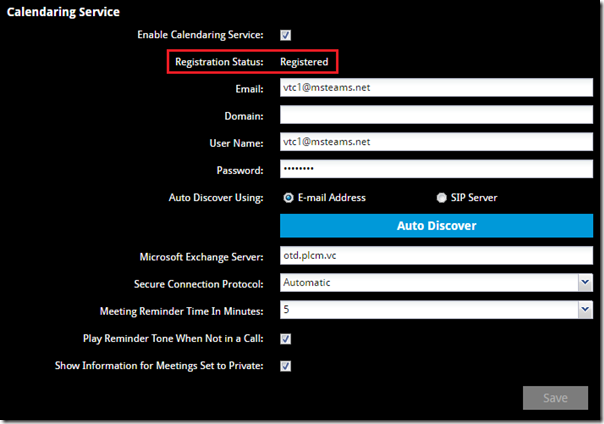
After saving the configuration the Registration Status will typically read either Not Connected or Registration Failed for up to 30 seconds while it is attempting to sign-in via Exchange Web Services. Once successful the status will automatically update to Registered.
If the mailbox has been invited to any scheduled meetings then the connected endpoint will now display those invitations on the calendar.
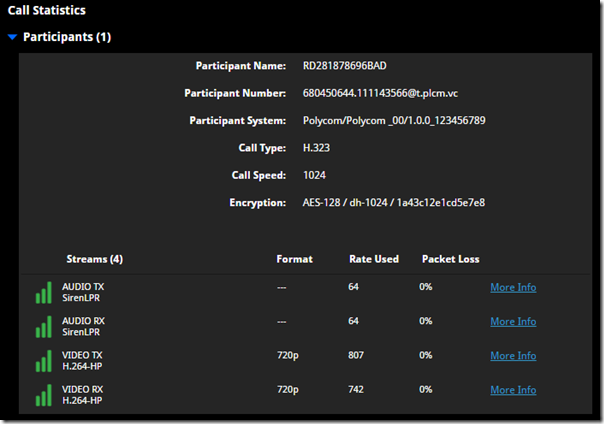
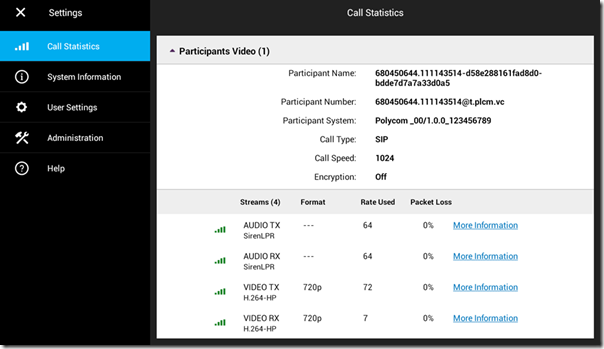
Furthermore, If any of those meetings are Skype for Business or Teams meetings scheduled by a user enabled for the RealConnect service then the Join button will be displayed, providing the simple One Touch Dial experience used to connect the endpoint directly into the scheduled meeting. The following Call Statistics details from the Group Series show a successful H.323 video call into the RealConnect for Microsoft Teams service (as denoted by the t.plcm.vc domain name in the call string).
At this point the standard setup is complete for any Polycom endpoints which are not natively registered to Skype for Business. In fact the Group Series used in this article was reset to factory defaults just prior to this configuration and the meeting was successfully joined simply by placing an H.323 video call after configuring the calendar.
Service Account Configurations
The configuration above simply uses the service’s default capabilities to automatically locate the source mailbox in Exchange Online via standard autodiscover processes. The mailbox credentials are stored on the endpoint and provided to the OTD service which uses pass-through authentication to connect to the mailbox and then process the invite. The same automatic process can be used with a service account, given that pass-through authentication is utilized (Option 1). Yet for proxy authentication (Option 2) some additional configuration is required to create new sets of credentials for each device as well as connect OTD to the Exchange organization and store the service account credentials.
Create Service Account
Both options outlined above can utilize the same single service account (e.g. otd@msteams.net), so perform these steps to create the new account and delegate permissions to the resource mailboxes accordingly for either option.
This service account must have a mailbox even though its own mailbox is never actually used throughout the OTD process. Exchange can only delegate mailbox permission to other mailbox-enabled accounts, hence the need for the license.
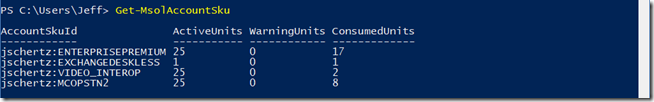
- Using the same process as outlined in the first section connect to both Exchange Online and the MSOnline PowerShell modules and then execute the Get-MsolAccountSku cmdlet to list all available license options currently applied to the Office 365 tenant.
Get-MsolAccountSku
The example tenant in this article has available Enterprise E5 licenses (ENTERPRISEPREMIUM), which is clearly overkill for this requirement. As suggested above a less expensive option of Exchange Online Kiosk (EXCHANGEDESKLESS) can be used instead. (As seen above the single Kiosk license in this tenant has already been assigned to another user, so for the purposes of this article one of the free E5 licenses will be used.)
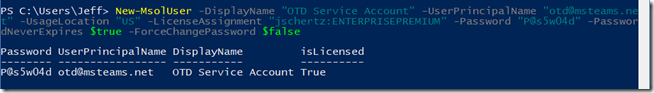
- Run the following New-MsolUser command to create a new user account which will be used by the OTD service to connect to Exchange over Exchange Web Services. Update the red text in the example below with the desired Display Name, User Principal Name, Usage Location (appropriate two-letter country code), License Assignment, and Password.
New-MsolUser -DisplayName “OTD Service Account” -UserPrincipalName “otd@msteams.net” -UsageLocation “US” -LicenseAssignment “jschertz:ENTERPRISEPREMIUM” -Password “P@s5w04d” -PasswordNeverExpires $true -ForceChangePassword $false
Delegate Mailbox Permissions
In order to use the new service account to access each and every resource mailbox it will need to be delegated the appropriate permissions to each mailbox. The only rights this account requires is Read access to just the Calendar folder in each mailbox.
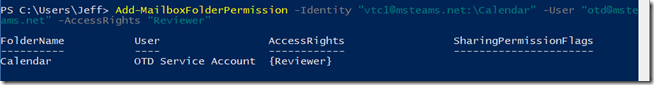
- Run the Add-MailboxPermission command by providing the Identity of the desired source mailbox, as well as the User Principal Name of the newly created service account.
Add-MailboxFolderPermission -Identity “vtc1@msteams.net:\Calendar” -User “otd@msteams.net” -AccessRights “Reviewer”
If needed, repeat this process to delegate permissions for each room mailbox’s Calendar to the single service account.
Verify Mailbox Permissions
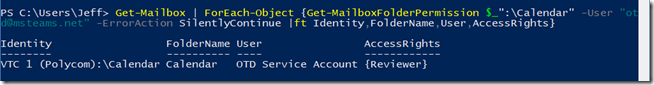
Once all mailboxes are configured the following optional cmdlet can be used to report which mailboxes in the entire organization the service account has access to.
Run the following command to query every mailbox in the organization to see all mailboxes the target account has been assigned permissions to.
Get-Mailbox | ForEach-Object {Get-MailboxFolderPermission $_”:\Calendar” -User “otd@msteams.net” -ErrorAction SilentlyContinue |ft Identity,FolderName,User,AccessRights}
This completes the requisite environment configuration and now the One Touch Dial Service can be setup and enabled.
Option 1: Pass-through Authentication
The first option available to use the service account requires no additional configuration. Simply use the service account’s username and password in the endpoint’s calendar configuration while still pointing to the desired.
- Connect to the web management interface on the Group Series endpoint and then navigate to the Admin Settings > Calendaring Service menu.
- Enter the Email address of the associated resource mailbox (e.g. vtc1@msteams.net), but provide the service account’s User Name (e.g. otd@msteams.net), and Password for the desired resource mailbox. (Leave the Domain field blank as the User Principal Name format should be used in the User Name field which already includes the domain name.)
- In the Microsoft Exchange Server field enter the Polycom One Touch Dial service FQDN of otd.plcm.vc and then click Save.
After saving the configuration the Registration Status will typically read either Not Connected or Registration Failed for up to 30 seconds while it is attempting to sign-in via Exchange Web Services. Once successful the status will automatically update to Registered.
- Check the endpoint’s calendar to verify any previously scheduled meetings are now displayed, and if any are a Skype for Business or Microsoft Teams meeting created by a RealConnect-licensed scheduler then a Join button should also appear.
In the example above a daily reoccurring Teams Meetings has been scheduled and the VTC1 mailbox was previously invited.
-
Select the Join button on the Group Series to connect to the scheduled meeting.
As this example meeting is a Team Meeting hosted in a tenant where the lobby bypass for VTCs has been enabled then the call connected directly into the empty meeting. Reviewing the call statistics shows the standards-based call (in this case SIP) matches the information shown in the original invitation.
Option 2: Proxy Authentication
The second option here will require additional configuration. The OTD service portal will be leveraged to store the service account credentials as well as define a second set of credentials to be used on the endpoint. This approach uses two separate accounts for adhering to any IT policies related to knowledge of service account credentials being delineated among different teams. Essentially and administrator can configure the overall solution while help desk personnel can be given only the local credentials which will only function through the proxy. They cannot be used to access the source mailbox directly in Exchange.
- Open the Polycom One Touch Dial service portal (https://otd.plcm.vc/) in a browser and then click the Sign In button.
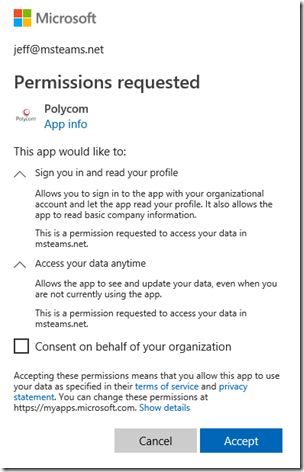
- Click the Sign in with Microsoft button and then enter the credentials of the account which was enabled for access (e.g. jeff@msteams.net).
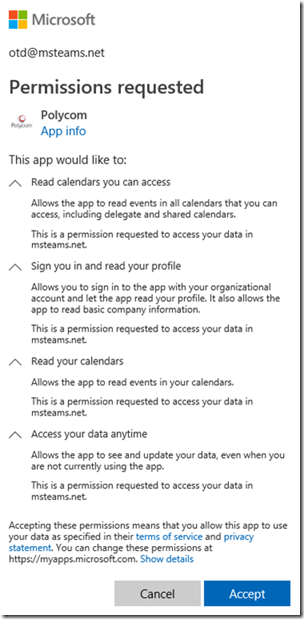
The first time that an authorized user signs into the portal a prompt will appear requesting permission for the Polycom app to sign in on behalf of and read the user’s profile information and data.
- Review the requested permissions and then click the Accept button. (If the “Consent on behalf of your organization” option appears it can be ignored as each user account authorized for the OTD portal will receive this same one-time prompt. If desired, an administrator can select this option now and other accounts will not be prompted when they first sign in. The behavior of the service is not impacted either way.)
-
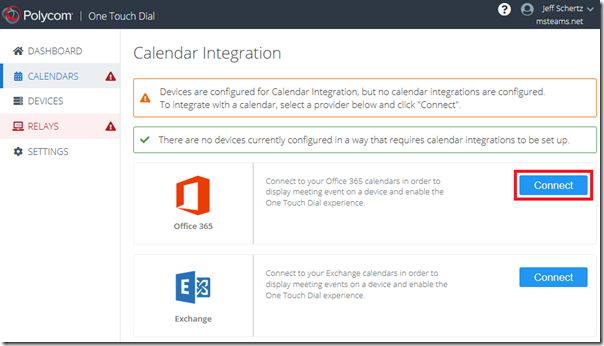
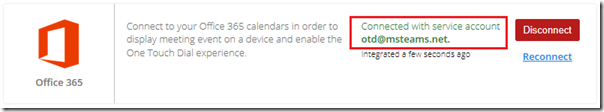
Click on the Calendars section and then click Connect next to the appropriate Exchange option. (Office 365 is used for connectivity to resource mailboxes hosted in Exchange Online and Exchange is used for connectivity to Exchange Server deployments. As this article is utilizing Exchange Online mailboxes then the Office 365 option will be selected.)
-
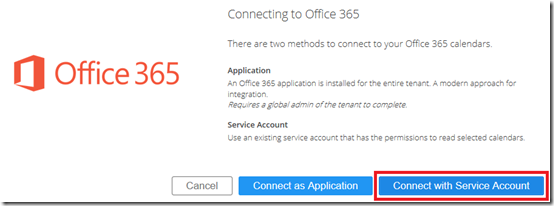
Select Connect with Service Account. (It is not recommended to utilize the Application approach given that permissions to more than just what was specifically delegated would be granted to the OTD service in the selected tenant.)
When the Connect with Service Account option is selected a Microsoft login window will appear. This authentication prompt is used to store the service account credentials into the OTD portal so it is important to enter the correct information here.
- Enter the username and password of the service account which was created earlier (e.g. otd@msteams.net) aa
- Review the requested permissions and then click the Accept button.
If successful the connection status for Office 365 will display the name of the account currently being used to communicate with Exchange Online.
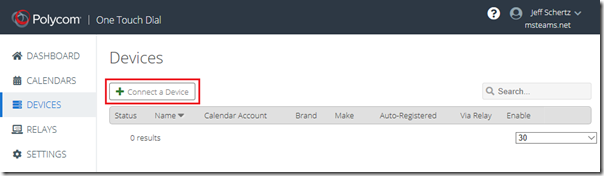
- Select Devices from the navigation menu and then click the Connect a Device button.
- Select the appropriate endpoint; in this example click the RealPresence Group Series button.
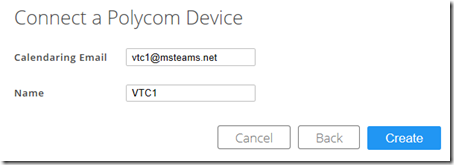
- In the Calendaring Email field enter the email address of the resource mailbox for the desired endpoint (eg. vtc1@msteams.net), enter a descriptive name in the Name field (e.g. VTC1), and then click Create.
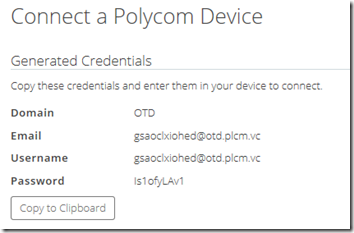
The next window will display a set of automatically generated credentials to use on the associated endpoint to authenticate to the OTD service with. The username is randomly selected and cannot be changed or customized. The password can be reset in a later step if desired.
- Click on the Copy to Clipboard button and then paste the details into a new text file for later use.
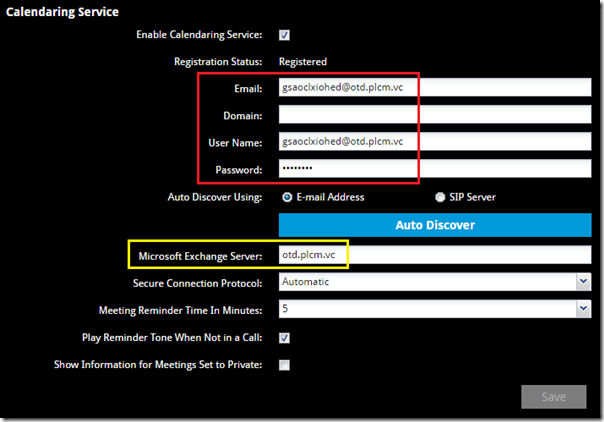
- Connect to the web management interface on the Group Series endpoint and then navigate to the Admin Settings > Calendaring Service menu.
- In both the Email and User Name fields enter the email address created by the portal in the previous step (e.g. gsaoclxiohed@otd.plcm.vc).
- Leave the Domain field blank as it is not used for this configuration.
- Enter the password as provided in the previous step (e.g. Is1ofyLAv1).
- In the Microsoft Exchange Server field enter the Polycom One Touch Dial service FQDN of otd.plcm.vc and then click Save.
After saving the configuration the Registration Status will typically read either Not Connected or Registration Failed for up to 30 seconds while it is attempting to sign-in via Exchange Web Services. Once successful the status will automatically update to Registered.
![image_thumb[16] image_thumb[16]](http://blog.schertz.name/wp-content/uploads/2018/11/image_thumb16_thumb.png)
![image_thumb[19] image_thumb[19]](http://blog.schertz.name/wp-content/uploads/2018/11/image_thumb19_thumb.png)

So it looks like from this excellent guide and Polycom’s website, the Group Series finally has support for using RealConnect for Teams. Is that correct?
“Furthermore, If any of those meetings are Skype for Business or Teams meetings scheduled by a user enabled for the RealConnect service then the Join button will be displayed, providing the simple One Touch Dial experience used to connect the endpoint directly into the scheduled meeting.”
Do each of my users need to be enabled for RealConnect or just the Office 365 service accounts being used to connect to EWS?
Dirk, Yes, the Group Series can join Teams meetings via RealConnect and has been able to for the past few months. The users themselves (who schedule the Teams meetings) will need to be enabled for RealConnect for Teams. This is simply a policy setting and not a license like SFB used (as outlined in the article I posted before this one) so anyone and everyone in the org can have it. The service account in this article is simply used for accessing mailboxes for invitation retrieval by the endpoints.
Been following and it’s great article
Currently we have RealConnect for SfB and everything goes well with Group Series since Microsoft licensed enable so Join Meeting wasn’t an issue until we are considering moving to Teams.
For Option 1 with service account, do we need to purchase additional OTD or just simply follow the guide create account, point RPG to otd.plcm.vc will do? As of now I don’t have any official OTD account from Polycom yet..
OTD functionality is included with your RealConnect licenses, so just go ahead and configure the Group Series as I show in Option 1.
You can find the official documentation for all Polycom cloud services here: https://cloudsupport.polycom.com/Services/ (select the Documentation section).
Yes and it work seamlessly
Just a quick note then the Group Series with Skype interop license enabled it will no longer in use, because of how OTD provision the dialstring method.
Correct, OTD is to be used with the RealConnect service. If you plan to stay registered to SfB you’ll want to keep the Calendaring service pointed directly at Exchange as the GS natively understands regular Skype Meetings.
Great Article! We predominantly use Cisco VTC’s in our environment and are piloting Microsoft Teams on a limited scale.The Polycom OTD portal seems to configured successfully based on successful connectivity to Polycom Cloud Relay and I have a Registered Cisco VTC that indicates the status as Connected”. After using the Teams Client to schedule a Meeting that includes a Cisco VTC, I am not seeing the “JOIN” button on the Cisco VTC. What am I missing or not doing right?
Thanks,
Naveen
If the invitation is showing up on the calendar, but no Join button appears there can be a few reasons. Most commonly it is that the resource mailbox used by the system is not correctly configured; typically the CalendarProcessing parameters for -DeleteComments and -DeleteSubject are incorrectly set to ‘$true’. These must both be set to ‘$false’ otherwise Exchange will erase the subject and body of the meeting invitation and then OTD will have no information on the meeting to process when it retrieves the invite on behalf of the endpoint. This article explains this above.
We are also predominately Cisco at our office. I am also using Polycom Cloud Relay. I have the JOIN button showing up on my Cisco touch panels however when I press it it only connects me to the RealConnect lobby where I then have to enter the Teams conference ID. I have my tenant setup to have VTCs bypass the lobby. I also have meeting permissions setup to allow EVERYBODY to join my meeting. Any ideas?
If you are being prompted for the Conference ID then you are not in the meeting lobby but are connected to the generic entry queue. That means the endpoint is only getting connected to the “tenantKey@t.plcm.vc” destination (e.g. 123456@t.plcm.vc), not the “tenantKey.confID@t.plcm.vc” destination (e.g. 123456.987654321@t.plcm.vc). This could be related to dial plan configuration if your Cisco endpoint is registered to VCS or a similar platform.
We are having the problem of our Crestron not showing a Join button but only for meetings that certain organizers invite the resource to. What is it in a Teams user profile in Exchange that may cause this? Is the issue even in Exchange at all? Thanks for any insight!
If you are referring to a Crestron room controller which is integrated with a standard Pol codec (like Group Series, Studio X, etc) then this likely is related to the Crestron controller programming and I can’t offer any guidance here as whomever set that up for you will need to address it. If you are referring to a Crestron MTR then that has nothing to do with the Poly OTD service.
Minor correction (I believe):
“These must both be set to ‘$true’ otherwise Exchange will erase the subject and body of the meeting invitation and then OTD will have no information on the meeting to process when it retrieves the invite on behalf of the endpoint.”
DeleteComments and DeleteSubject must both be set to false, as in do not delete these. I believe this is what Jeff meant, I’m just pointing it out in case it isn’t obvious to anyone.
You know you’ve made a valuable blog post when people are still poring over its details 2 years later.
Good catch! I just fixed the typo in my previous comment.
Hello Jeff,
have you noticed any issues for any users in your company that the email invitation consisting Teams Interop part was converted while sent from Outlook client in a way that SIP URI was recognized at device calendar as mailto: link and so the OBTP service didn’t recognized correctly Teams meeting URI so couldn’t create a correct join button?
I’ve not seen that but if anything is modifying the body of the invitation than it’s possible that the service cannot recognize the URI correctly. Are their Outlook add-ins or is SMTP mail delivery involved in the path?
Hi Jeff,
Curious whether you know if the RealConnect cloud service can attach to O365 and on-premise Skype simultaneously? I successfully integrated both but there’s no spot to tell the service that an account should use one integration or the other.
As this is posted on the OTD article I assume you are asking about the calendaring functionality. OTD does not currently support connecting to both Exchange Server and Exchange Online at the same time. Guidance is to locate all room resource mailboxes in the same platform and then connect OTD to that single platform.
Does an HDX registered to OTD have the capability to share content with a group 500 registered to RPRM? I can share from Group500 to HDX but i cant share HDX to Group.
Thanks
OTD only provides calendar registration. Both the Group Series and HDX share the same standards-based codecs, but it is unclear how you are connecting them together. If they can negotiate a peer call then content sharing works in both directions, but since you mentioned OTD I suspect you may be mixing solutions.
[…] Polycom One Touch Dial Service – explains what this ancillary service is, how it works, and provides detailed configuration steps for using it with Polycom VTCs. (A future article will cover the configuration for Cisco VTCs.) […]
Hi Jeff – love the site. We currently have Polycom Trio 8800 and Group Series 500 running on SfB Online
Could you please help address the below?
Is it possible to have the Group Series 500 with RealPresence Touch panel, permanently connected to a PC/laptop so that it can present content via HDMI for local participants and or in a sfb meeting?
If we wanted to provide the ability to connect to Zoom meetings via the calendar or provide a one touch experience to connect to Zoom, would the cloud service called One Touch Dial provide this ?
Or is it possible to simply add a second line to Dial into Zoom meetings like you can setup with the Trio 8800s ?
Hi Jeff
Does the Group Series provide the option for a second line, similar to the Trio 8800 so that this second line can provide the option to dial Zoom meetings as an example?
Similar, but not exactly the same. The Trio supports several concurrent registrations (Hybrid Registration), but they are all only SIP. The Group Series supports only two (Dual Registration) with a single SIP registration (which would be occupied by the SfB registration) and a single H.323 registration. The H.323 configuration can be used to leverage Zoom’s Cloud Room Connector which supports H.323.
And yes, the One Touch Dial Service can be used to join Zoom meetings directly from the Group Series calendar.
Hi Jeff
Does RealConnect service only work when the invites are generated internal to your organization? i.e. if a 3rd party sends a Skype for Business or Teams invite, and we’ve enabled OTD etc. – could I join from a Group Series?
The issue we have at the moment, is that we use the SIP registration on the Group Series with a traditional PBX, so that it can make telephone calls.
Looking for a way to join SfB / Teams meetings from my codec, without having to register it to SfB under the SIP settings.
Thanks, great blog btw, we use it regularly
Graeme
No, if you receive RealConnect-enabled invitations from another organization using the service then your own endpoints may be able to join directly fro the calendar. When using RealConnect it’s typically best to not SIP-register to Skype for Business anymore, but if you need it for PBX/PSTN integration then you don’t have another option.
Hi Jeff,
Thank you for this very informative article about Polycom OTD. We are currently using a demo trial for Polycom OTD and having some issue using “Option 1: Pass-through Authentication.” However, Auto registration and Proxy Authentication works well and tested OK.
If we are using the Pass-through authentication, our multiple Group Series devices will register completely but from the OTD portal, the calendaring and authentication information will mix up with other devices.
We have opened a case to Polycom Support and they are investigating the issue. Do you happen to experience this kind of problem? Thank you
I have not seen that before, but contacting support is to best course of action.
I have a OTD On-premise and Easy Schedule in Outlook … I´m migrating users of Lync 2013 to O365…;
– I can use easy schedule and OTD On-Premise, for use calendar in hybrid form?
I have Polycom Group Series and, HDX.
If yes, I need add one new count of service and one new count of room inside of O365 for user already migrated, correct? And inside of OTD (Workflow) add new count service ? Only ?
Can you help me ?
This depends on if you are using RealConnect or another meeting solution with Easy Scheduler. The OTD service is intend for RealConnect Service utilization, so if you are leveraging on-premises Polycom video infrastructure you retain the on-premises Workflow Server (which runs OTD, Easy Scheduler) reagardless of where the SfB users are homed.
Hi Jeff,
I don’t know how would we survive without your articles! Thanks a lot for the job you are doing!
Despite of your detailed guidelines I managed to get in trouble with enabling OTD on Polycom Trio. It’s registered as Skype for Business Online endpoint, and everything works fine if Autodiscovery is enabled in Exchange configuration. But if I specify OTD server there, the endpoint fails to connect to the calendar. We are using standard configuration, i.e. the endpoint is using the user account associated with the room mailbox.
Vadim, are you attempting to use RealConnect for Teams meetings with the Trio while it’s also registered natively to SfB Online? If so, then the Trio should not be using the OTD service and instead has it’s own internal configuration options to handle meeting processing in a hybrid configuration scenario. I’m working on a blog article to explain how that works. If you are simply using the Trio with SfB and not RealConnect then you should not even point the Trio to the OTD service. In either case, don’t point the Trio to OTD, leave Exchange autodiscover on so that it points directly to its mailbox.
Hi Jeff,
Many thanks to you for the great articles.
If Trio don’t have native registration to Skype, how he can then get OTD? You can give up manual Exchange adres but where i can set up room account for this device? Environment is Teams only.
There is a configuration available for the Trio to register to Exchange only. A pending blog article will cover this, but you can get that configuration from Poly support.
Hi Jeff,
Did you ever publish the above article?
I have Trio 8800s that are natively registered to SfB and have a second line for RealConnect. However its not clear how to get OTD working for the RealConnect meetings in this scnario.
I use the SfB for PSTN/PBX.
No, I have not. Typically the Trio would not even use the OTD service as it can parse RealConnect-enabled Skype and Teams invites.
Hello Jeff,
Great guide. i was able to test successfully the OTD service for my company thanks to you. We are now testing the RealConnect for Teams as our company is moving to Teams as the only internal collaboration tool.
I still have a question : is it possible de hide the subject of the meeting on the home screen just for confidentiality purpose?
Thank you
Nathaniel
Yes, if you go to the Settings section in the OTD admin portal you can toggle multiple privacy-related settings, including having OTD strip the subject name from invites.
Hi Jeff!
yes you’re right ! thank you !!!
Any feedback with HDX endpoints : it seems to be it only support relay mode ! do you confirm?
I haven’t tested an HDX, but it does not support direct registration to Exchange Online so pass-through authentication may not work either.
Great job Jeff!!! Keep it up.. Good stuff!! BB
Great To do’s Jeff.
Currently trying to implement a solution with Trio, visual+ and RealConnect.
We only have Microsoft Teams and Office 365 cloud, nothing on prem.
And setting this up I have come up with 2 scenarios:
a) Keep the phones registred with SfB and everything works fine the invites the meetings, except when you share the screen from laptop, that doesn’t show on the Visual+
(I’m assuming it’s because in this scenario I’m not leveraging the RealConnect ?)
b) I setup the OTD , connect to our instance the Trio logs in with OTD no problem.
Issue: we don’t have a SIP provider so the line is not setup therefore the videoconferencing doesn’t work.
Am I wrong in assuming that using OTD we would need a SIP connection configure with some kind of carrier ?
Thank you very much.
Best Regards.
a) Correct. Technically video shouldn’t even work but Microsoft is not blocking via through the ‘audio’ gateway between SfBO and Teams. It drives me crazy they are incapable of stripping the m=video from SDP to fix this issue as it confuses everyone. You should be using RealConnect (which is free for a year with hat Trio).
b) I typically wouldn’t point the Trio to the OTD service as it can parse RealConnect invitations natively. You can contact your Poly sales/support teams for details on that configuration. Also there is no need to register to anything as you can make SIP calls directly into RealConnect.
Hello Jeff,
First of all, many thanks for all this articles and details we can easily find. Really good job.
At the moment, I am looking for a solution to permit Poly endpoints, to have an OBTP-like feature. From what I read, I am quick lost I would say … Is there a way to use Poly Workflow Server, to permit Poly endpoints to retrieve their meeting in calendars (Exchange, 0365, Google Calendar …) and to have corresponding “JOIN” button for meeting they are including in ?
Do you confirm Workflow Server permit here to build the “JOIN” button, or can endpoints directly create such button when access to calendars ?
Many thanks in advance for your feedback,
Regards
Gil
It depends. Each Poly endpoint is capable of creating a ‘Join’ button by itself, but what that button can be used for is different. The Group Series can join Skype for Business meetings natively on it’s own, but needs to leverage either Workflow server or the OTD Service to join Skype and Teams meetings using RealConnect. The Trio is capable of joining native Skype and Skype/Teams via RealConnect by itself, as long as the meeting invite is in English (foreign language support requires pointing the Trio to Workflow Server or the OTD Service.
Hi,
We have Polycom Trio 8800 with Visual+ and we are using RealConnect + OTD.
Sometimes calendar lose the JOIN button near to the meeting and it appers after some secounds or minutes! Sometimes we want to start the meetiing and Join button is not available in the moment that we need.
Any help?
Unless you need to support Teams meeting in non-English languages you don’t need to use the OTD service at all with the Trio, it can parse RealConnect-enabled Teams meetings natively. See this article for the proper configuration: http://blog.schertz.name/2019/08/poly-trio-with-microsoft-teams/
Hi Jeff:
Thanks so much for your articles. We’re slowing making progress integrating our Group Series to Teams. We’re not there yet.
We’re activated on https://webapp.plcm.vc
I can test call 7357@test.plcm.vc successfully
I’ve configured OneTouchDial as an application to 365 and the tests are successful
I’ve run the powershell commands to set up the InteropServiceProvider
So I’m close.
Yet – I cannot register our Group Series to the Room Resource via otd.plcm.vc
It either can’t find the server or is listed as not registered.
I can, however, get the calendar working via outlook.office365.com and it comes up very quickly. Since this might be a firewall issue, I’ve added the following addresses to our pre-existing “VC Allow” group
40.121.8.241
20.42.26.252
plcm.vc
otd.plcm.vc
prod-plcm-teams.trafficmanager.net
t.plcm.vc
teams-prod-scus.plcm.vc
But nothing happens. Do you have any suggestions that could point me in the right direction?
Thanks.
Adam, please reach out to your support contact as it’s possible that the One Touch Dial service is not provisioned or configured correctly for your tenant.
FYI – I ultimately resolved this issue. The credentials we were using in the O365 – that worked – were an old version of our domain name (they do change over the years). They worked in O365, but they wouldn’t work in OTD. I reset the name in active directory to our most current domain name – confirmed that it worked in O365 – and then, voila, it also worked in OTD. Had nothing to do with the firewall.
Also, had a slightly different situation in our London office. Could not register the units with either O365 or OTD. Again, at first I thought it was a firewall issue. But it wasn’t. It turned out that the unit came to use from a reseller who left the security profile at Maximum – which is DoD grade security. However, the default from the factory is supposed to be minimum. Once I changed the profile to the proper default – OTD registered.
I think these are both obscure situations – that just require constant troubleshooting and learning the GroupSeries, until you get it. While it takes a long time, you end up understanding the process better.
Hi Adam,
Have you solved your problem? Was it really the firewall?
We have something similar with one of our customers who is setting up the trial. Everything seems done right but OTD is not registering although mailbox registers directly to O365 server as in your case. Tried all approaches – passthrough without OTD portal configuration, using an application method and also as a service account. And i gues it’s not the firewall issue since i tried to register using my codec (also unsuccessfully) which registers fine with my RC account.
Thanks.
This issue could be related to the use of multiple domain names in the mailboxes SMTP and UPN addresses. I suggest contacting Poly support as we may need to update your tenant in OTD to support additional domains.
First things first – thank you Jeff for great article (as usual).
I wanted to post a quick solution to one problem, that some people may find useful.
When you are trying to use below command:
Add-MailboxFolderPermission -Identity “vtc1@msteams.net:\Calendar” -User “otd@msteams.net” -AccessRights “Reviewer”
And you get an error in response:
The operation couldn’t be performed because ‘vtc1@msteams.net:\Calendar’ couldn’t be found.
In my case instead of “Calendar” folder I had to use LOCALISED name (since I’m from Poland – it was “Kalendarz”).
It’s been suggested by Martina in below topic:
https://social.technet.microsoft.com/Forums/ie/en-US/c2b57516-788b-4341-8aad-8e8f463c7c20/using-addmailboxfolderpermission-operation-couldnt-be-performed?forum=exchangesvradmin
Good tip! I didn’t realize that language location came into play here, but that makes sense based on how the objects are labeled in the container.
Hi Jeff:
I have two Group Series in my Washington Office up and running with OTD and RealConnect and Teams and it’s a thing of beauty.
I have two similar units in London and I can’t get them to register to their room resource calendar via OTD. I’ve tested the credentials on my DC office – and they work, which leads me to believe I have a firewall (SonicWall) issue.
While I’m no network engineer, I’ve added as many permutations of otd.plcm.vc to the white list to my 500 series. But I can’t register to either 365 or OTD.
Could you list or direct me to the addresses I need to white list for OTD and RealConnect for Teams? Is there some internal whitelist on the 500 that I might be overlooking?
Thanks for any help you can provide
Adam in DC
Simply run an nslookup on
otd.plcm.vcto resolve the current IP address(es). (These do not change often, but it’s possible as they are not yet in a dedicated Azure IP space.) Currently that FQDN can resolve to one of two different load balanced hosts, so the response will depend on your geographical location. Thus, your Washington office (assuming Washington State and not D.C.) may currently be resolving to 52.160.40.218 which is located in an Azure datacenter in the Western US, but the London office is likely resolving to 40.71.11.136/40.121.8.241 which are an Eastern US Azure datacenter.Follow up – as I mentioned above in another post – it turned out that the unit was shipped to us with the security profile set on “Maximum.” Maximum is by design very restrictive. Once I changed the profile to the default setting – OTD worked. It had nothing to do with the firewall or networking.
One cautionary note – when you change the security profile your “user profiles” are blown away. This includes any admin logins you have to get into the unit. So you must re-set your admin logins before you log out, or you will be locked out of the unit – and will have to perform a factory reset to gain re-entry.
Hi Jeff,
To clear things up:
1. Do we need One Touch Dial in order to use RPG700 with Teams meeting via Real Connect service?
2. Is Cloud Relay server required for that?
3. Configured OTD by activation O365 application integration and adding email of RPG’s mailbox. Have following error on RPG when adding exchange server “Unable to find a server”
Thanks,
Sam
1. Yes, One Touch Dial will parse various invitations that the Group Series does not natively understand (e.g. RealConnect for SfBO and Teams invites).
2. No, the Cloud Relay (in terms of One Touch Dial) is only used for Cisco endpoints (which are not EWS clients like Poly endpoints) and need the messages pushed down to them from Azure.
3. Do not use the Application method unless you are testing this in a non-production tenant as the application will receive read permissions to every mailbox in the organization. You should either use pass-through authentication (no portal configuration required for Exchange Online mailboxes) or define a service account as shown in the Cisco OTD article.
Might found an error. Our default domain is different than what RPG units are using due to inability to web sign in to use MFA. Do you know if there is a way to add additional domain that we own and use in Office 365 tenant to OTD service? Or should OTD pickup all domains from O365 tenant that we own?
It should have picked up all domains during onboarding, but I suggest opening a support ticket to have the missing domain(s) manually entered into your configuration.
[…] to provide administrative access for additional user accounts to the management portal for the Poly One Touch Dial (OTD) Service. Typically when initially onboarding the service for a tenant one or more Microsoft online […]
Hi Jeff,
We have integrated the Polycom HDX series with the hosted OTD. Calenderaing service in the HDX is not stable , every few minutes like 2, 3, 5 or 8 minutes the calendaring service in the HDX system goes down and during this time if we try to access the HDX calendare meeting details to Join the meeting, meeting info is not displayed. We are running on latest software for all HDX and we have same issue in our offices in the UK, Netherlands, USA, Switzerland and in Singapore. We have raised ticket with Poly cloud services and also with HDX support team. Below are the errors in all HDX systems . After couple of minutes the Calendaring service in HDX will be up on its own. Do you have any thoughts on this, please.
2019-09-27 06:31:42 INFO jvm: pc[0]: UI: asyn: SECURITY: ConfigurationManager calendarloginerror.dat = {CALENDAR_CANNOT_CONNECT_TO_SERVER}
2019-09-27 06:31:42 DEBUG jvm: pc[0]: UI: asyn: TelnetClient: APIClient.flush(): configchange: calendarloginstatus FAILURE
2019-09-27 06:31:42 DEBUG jvm: pc[0]: UI: asyn: TelnetClient: APIClient.flush(): configchange: calendarloginerror CALENDAR_CANNOT_CONNECT_TO_SERVER
2019-09-27 06:31:42 INFO psh: API:ttyFPGAS4:211212:OUT:configchange: calendarloginerror CALENDAR_CANNOT_CONNECT_TO_SERVER
Thanks
Sundar
Hi
We also have this issue when using normal calendaring services. I tried to switch over to OTD, but where I need to add the mailbox from OTD on the endpoints calendaring service, it is grayed out. I can’t update it. Seems when the unit is provisioned by RPRM it gets “locked down”?
Hi Jeff:
I just opened up a ticket with support on this, and posted a question in the community. I’m using PRTG monitoring software to monitor my 4 Group Series. Using the SNMP MIB downloaded from the 500 – I was able to import the Exchange Calendaring service sensors into PTRG and I can now monitor the up/down state of OTD registration. This allows us to be very proactive and, I think, is a huge thing.
However, we had our first outage! This past Friday, the units de-registered from 6:00 to 8:00 PM EST. And then they registered again. Two in DC. Two in London. My inbox filled up with alerts. And then it was over as quickly as it began.
My question is – is there a notification service from Poly/RealConnect that will let us know when the system is unavailable? For all I know, it could have been an Office 365/Azure issue – and had nothing to do with Poly/RealConnect. Nonetheless, if we’re all hitching our wagons to Teams – this will be an important thing to nail down.
Thanks for any suggestions you can offer.
You can sign up for alerts on status.plcm.vc
Hello Jeff, I would first like to say that your articles have been useful in my job.
I have a 8800 Trio with teams + realconnect, working well video calls. The problem is with the OTD,
the device status is only “unreachable”. Calendar Integration is connected and tested OK,
the calendar and credential device settings are checked and ok, but the device doesn´t register.
Would you have any tips to help me in this question?
Thanks
Don’t use the Trio with OTD service (unless you need to support non-English meeting invites, until that is fixed in upcoming Trio release). Configure the Trio to handle RealConnect invites natively as I’ve outlined in http://blog.schertz.name/2019/08/poly-trio-with-microsoft-teams/
Hi all,
I’m adminstrtor of OTD and i want to hide the subject off the meeting on the calendar,please help
BR
Simply go to the Settings section in the OTD admin portal and enable the “Hide Event Subject” option.
I have configure OTD integration to Office 365 with a service account. I have 2 group series one configured with manual registration (using OTD account) and one configured as auto-registration. Both work fine. I have few Trios configured in Hybrid mode (followed your great article) as Hybrid and works fine. Is my understanding correct that if I configure the Trios to use OTD service, I would be able to join Zoom, BlueJeans and other providers seamlessly using the Join button (by forwarding the meeting invite to the room calendar)? If so, can I have a Hybrid Trio configured with OTD? I tried to configure the Trio to use OTD as Exchange Server URL, but it does not connect to the Calendar.
Chris, the Trio supports invites from most of the same (and it may be literally the exact same) list of conferencing platforms as the One Touch Dial Service does. At this point I would use the Trio configuration options and point directly to Exchange, skipping the OTD service.
Hi Jeff,
On our Poly endpoints we want to use Proxy Authentication provided by OTD service for security reasons.
But we have same issue that Chris has – Group Series endpoints are registering to OTD fine, but Trio (v5.9.3.8724) fails to register with this error:
0619103914|auth |4|00|pHD(146)AuthServiceCallerEwsSvc
0619103914|app1 |5|00|[CAuthServiceEwsRsp::execute] Failed to get oAuth token with (400,Failed to Get UT)
0619103914|pgui |4|00|CEcLayoutMgr::readTokenData() reading token data from file
0619103914|pgui |4|00|Received token data of length ‘0’ for type ‘2’ from app for(0) sec
0619103914|pgui |4|00|Received token data in calendar with length ‘0’ and type is ‘2’
If I change exchange url from otd.plcm.vc to outlook.office365.com, then calendar works fine, but we don’t want to give out mailbox passwords. And based on this guide Trio should work with OTD: https://otd.plcm.vc/support/docs/devices/polycom-trio
So is this know “limitation” of the Trio or configuration issue?
If anything, I would expect Trio to handle registration with OTD better than Group Series.
Many thanks
Jenka
Don’t use the OTD service for the Trio. The Trio can perform the same rule processing actions as the OTD service provides so there’s no need to point the Trio to the OTD service.
Hi Chris,
I’m facing similar issue. Were you able to resolve it? if so, how?
Is there a list of Platforms that OTD will create the JOIN for?
Obviously – front and center is Teams. But I’ve also tested Zoom successfully. The key is to create the meeting request for the room device by copying and pasting the meeting url into the location field. OTD then scrapes that info and creates your Join button. This means that you are automatically placed into the meeting – rather than dumped into a lobby – and then manually type the meeting number to finally join. In other words – it’s awesome. But I can’t find a list of platforms that this works with.
I believe that BlueJeans, GoTo, and some obscure Amazon service are on the list. Thanks if you can provide one.
The current list of supported conferencing services can be seen in the Providers section of the Settings menu in the OTD portal. For example, here’s the list as of Nov 2019:
Skype for Business Server and Online (Native and RealConnect), Microsoft Teams (RealConnect), Microsoft Lync, Zoom GoToMeeting, BlueJeans, Amazon Chime, Cisco WebEx, Videxio, Google Meet.
Hi,
I have to regsitre a room with On-Premise resource MailBox to the OTD, This OTS has only CloudCalendar Server configured with O365.
My question how can i configure OTD to accept registration from rooms with On-Promise mailBox.
Thanks
Currently the OTD service officially supports mailboxes in one location, so it is recommended to host all resource mailboxes either on-premises (in Exchange Server) or online (in Exchange Online). If your resource mailboxes are split you can configure both Office 365 (Exchange Online) and Exchange Server (via EWS) in the OTD portal at the same time, but it’s possible that connections may not function correctly depending on the overall setup. I suggest contacting support for assistance with an Exchange Hybrid environment.
Hi Jeff, we doing the same thing but getting 2 issue.
invalid username, password or domain name
Calendar access not permitted it works and come up again after few days
unreachable it works and come up again after few days
I’m not sure if you are reporting issues getting into the admin portal or the devices themselves accessing their calendars through the service. But if you haven’t already opened up a support ticket for this then please do.
Hi Jeff
Great article!
I have a GroupSeries 500 currently registered to Skype on-prem. I’m about to move the account to Skype Online.
Is it possible to configure the GS500 to use RealConnect to join Teams meetings, but keep the GS registered to Skype?
My goal is to have the GS still natively join Skype meetings, but also join Teams meetings via RealConnect. (Similar to a Trio 8800 in Hybrid mode).
My issue is, if I de-register the GS from Skype Online, we lose the ability to call the GS500 directly from a Skype endpoint. In that case the GS500 is no good for anything except joining pre-scheduled meetings.
Am I thinking correctly?
Cheers
Jason
Yes, that is the correct path. Just leave the SIP configuration setup for Skype for Business registration, but also enable H.323 and set it as the preferred calling protocol. This will allow the GS to use H.323 to call into the RealConnect service to join Teams meetings (when configured to use the OTD service for calendaring), yet still use the native SIP-registration to SfB to join Skype meetings directly (not via RealConnect).
Jason,
Were you able to get this to work. I am attempting the exact same scenario. I’ve set H.323 as the preferred protocol for video calls with SIP secondary but my GS keeps uses RealConnect for both Skype Online and Teams meetings. Like you we would like to leave Skype Online Meetings a Native and unchanged experience.
Luke
Luke, it sounds like your Skype for Business meetings are also enabled for the RealConnect Service, meaning they too include the additional VTC details in the meeting invitation. In this case the One Touch Dial (OTD) service needs to be configured to ignore Skype Meetings and only process Teams meetings if your intent is to allow all Group Series endpoints using the OTD service to still leverage the native SIP-registration for joining Skype meetings. Sign in to the OTD portal (otd.plcm.vc) and then on the Settings page disable the Poly RealConnect with Skype for Business Online option under the Recognize Meeting Invitation – Providers section.
Hi Luke
Yes I got it working. Exactly the way Jeff mentioned.
Cheers
Nice article as usual, Jeff!
Just to be sure that I am understanding correctly, the OTC service is just to put the dial string onto the endpoint ‘Join’ button, and is not providing any interop gateway. If the endpoint is SIP-registered and is trying to join a Skype or Teams meeting, RealConnect is needed in addition to the OTD service, correct? And, OTD is included with the RealConnect licensing, but is that for both Poly and Cisco endpoints?
Correct, all OTD does is read the invite and then insert the proper dial string instructions into the invite that the requesting VTC will understand. OTD can provide this One Touch Dial experience to generate a functional ‘Join’ button on the VTC for a myriad of conferencing services with standards-based support or gateways (e.g. WebEx, Zoom, etc). RealConnect is the gateway for Microsoft UC platforms (Skype and Teams). The OTD licensing is included free with RealConnect licensing purchases, as well as free to Poly endpoints. So if you are a RealConnect customer than OTD is free for all VTCs (Poly and Cisco). If you are not a RealConnect customer and are just using OTD for joining WebEx meetings or Zoom meetings, or any other non-Microsoft platform than licenses for Poly endpoints are free, but licenses for Cisco endpoints would need to be purchased.
Hey Jeff,
A million thanks for the write up! It has been a savior for us to say the least. We are facing two issues and I can’t help to think that they are related. We were able to configure our Group Series for OTD using Teams, it works just as expected but that has broke Skype for us. One Touch no longer works for Skype if it’s working for Teams. We do not want to use RealConnect for Skype, but want to use “Mixed Mode” as you mentioned in one of your articles. I have shut off Poly RealConnect for SfBo and Server in the OTD portal.
So this is where I think it’s related. I cannot get my Devices to show “Connected” in the OTD Portal but here’s the kicker, I can get them to connect if I use my email address which is domain.com. Our VC endpoints all use domain.onmicrosoft.com. I am wondering if that is where the breakdown is occurring? Any insight or guidence would be greatly appreciated.
Shane, please open a support ticket on this issue as most likely your tenant configuration is missing the secondary domain which would generate an error in the OTD service. Support can remedy this, or email me directly with your domain name and I can take a look at it myself.
Hey Jeff,
That was it. The Orion team at Poly fixed it on there side and the devices finally show connected. Facing an additional issue based off your write up. You state that for mixed mode, the Dialing Preference should be:
V1 – IP H.323
V2 – SIP
A1 – IP H.323
A2 – SIP
I can’t get the to work when it’s configured that way. It works for Teams/RealConnect but for Native Skype it dials the PIN of the conference number and I get the – Couldn’t complete the call….
But if I configure like below both Teams\RealConnect and Native Skype meetings work:
V1 – SIP
V2 – IP H.323
A1 – SIP
A1 – H.323
I’m just trying to get the warm and fuzzy that this is fine or is there something else I need to check to make sure it matches your configuration?
Strange as that’s the opposite behavior that I’ve seen, but if it’s working for you then don’t mess with it 🙂
[…] the configuration for mailboxes for use with standards-based video conferencing solutions from Poly and Cisco which support Microsoft Exchange to display and join scheduled Skype and Teams […]
Hello Jeff,
Thank you for the great article. Is it possible for the Real Connect One Touch Dial to be configured as ‘Auto Dial’ due to the COVID-19 pandemic a lot of people are asking the question on how we can have No Touch Join that the meeting automatically connects at the scheduled start time.
Thank you!
No, the endpoint must start the call as it cannot receive a call from the service.
Jeff, many thanks for the very informative articles, they are lifesavers as always.
Quick clarification, so with RealConnect & OTD, its sole purpose
would be for a Group series or G7500 to only Join a pre-scheduled Teams meeting, correct?
I would not be able to initiate a point to point call
on the Group/G7500 itself to dial into a native Teams endpoint like a Crestron Flex, Logitech Tap or even my own Teams app on my laptop, is that right?
Correct, RealConnect only allows for a VTC to join a Teams meeting, there is no endpoint registration, directory, or peer calling capabilities. Only native Teams client/devices can do that.
Hello, Jeff realy nice article! May i ask you for a little help? So we have try to setup a new G7500 endpoint with Exchange server. I have create service account and resource mailbox. Then i grant permission on service account to read calendar on resource mailbox. Wich scenario is recommended for our setup? So i have try to configure endpoint by enable calendaring service and fill the required filed with :
1 Credentials generated from OTD portal, with no succes registration
2. Credentials of service account (created in our Exchange server), with status “Registered”
Now situation is as follow, on OTD portal i get this message when try to connect calendar:
“Configured with service account” hhhvc@hhhhhh.com.
Unable to access. Please try reconnecting and ensure account has proper permissions.
After that when i try option “Test Exchange Calendar Connectivity” Result: Success
We have try microsoft connectivity tool and was passed without errors. Error occured only when leave checkbox “Ignore trust for SSL” blank. If i enable this checkbox the passed succesfully.
Thank you in advance!
I recommend starting with the passthrough authentication portion first to validate connectivity and then moving to the proxy auth approach. Also you may want to use the app permissions model instead of the service account model now that Exchange Online supports app permission policies to be defined to limit the scope of object access.
Great blog, Jeff. I’ve managed to configure 6/7 of our RPG500 codec to use the OTD calendaring service.
The 7th and final one is struggling to locate the ‘otd.plcm.vc’ server and causing the registration to fail every time.
~There is no major firewall in this site, just a generic DrayTek. all usual ports are enabled. I’m at a loose end as to what else I could try? Be glad of your expertise please Jeff!
I would go with a factory reset on the GS and reconfigure it. This often clears up a problem when the configuration is correct but the device is not acting as though it is. Especially when all the others work fine (assuming same firmware version on all of them).
Hi Jeff
Thanks for all your articles on these topics, very detailed and insightful.
My scenario is I have a Trio 8800 with visual pro and trying to get it working in a 100% Teams environment now. I am looking at getting a Realconnect trial, and will follow your guide to set up hybrid registration alongside a normal sip connection to our VoIP provider.
My confusion comes over OTD, you’ve said in all the comments here that Trio wouldn’t need OTD? So in my set up we would simply set up real connect as per your other guide and this would pull through the resource mailboxes meeting invites and put them into the meetings list on the handset with the join option? Is there no extra config required? I would imagine we have to enter the mailbox credentials into the handset somewhere to log In to the mailbox?
Thanks
Correct, the Trio has the OTD intelligence built-in. If you are not using Skype for Business at all then the configuration would differ from what I’ve covered in an older article. You would leave the Trio in Generic Base Profile and then use the Exchange Calendaring configuration to setup calendar access directly to the target mailbox. This can be performed via the Trio’s web management UI.
Any idea why the EWS pointing to otd.plcm.vc takes long time to show the new calendar invites??
if its outlook.office365.com then its instant, when we switch it to otd it take more than 5mins to show the new booking invites in calendar of the touch screen in Group 500. thanks for clarifying it.
Although it can take a few seconds longer when going through the OTD service it shouldn’t be notably different.
We are using a Polycom Group Series device, but on the plattform it still says that it needs a Relay, even though we don’t have any Cisco VTC’s. Is there a reason for that?
Polycom VTCs cannot and do not communicate with the Cloud Relay, so I don’t know where you are reading that.
Hi jeff, can you help, our client using OTD before and now got issue with joining using OTD when click join button it goes to the call but no “welcome to realconnect” displayed and suddenly it drops the call. But if join using VTC Dialing string manually call is successfully. Can you assist us?
The Join button must be dialing a different string than what you are manually testing with. Use the RealConnect reporting portal to compare the dial strings used between what is manually dialed and what the button is dialing.
Hi Jeff,
We are tying to install cloud relay for using cisco endpoints but we keep getting error on the application status. It is never successful:
It says calendar_relay is rejected.there is no means to upload the error screenshot here.
Make sure you have purchased a license to use the associated Poly services as if your organization has not yet been onboarded by Poly then the Cloud Relay will not be able to connect to the cloud service.
Hi Jeff,
we acquired our first OTD licenses, setup has been performed reading an Office 365 mailbox to generate Join buttons on Cisco SX20. It does work, but …
1. Cancelled meetings show up on the meeting room screen, with a sentence saying “Meeting will automatically connect” ! We would like OTD to ignore cancelled meetings. What should we do ?
2. The nice “dark green Join meeting button” appears nicely on the tablet when the room has been invited in a Teams (joined using Realconnect) or Starleaf meeting, and it works nicely. But a “light green Join meeting button” also appears on the touchscreen when there is a room booking without invite to an online meeting; and of course, you can tap the button but there is no result. How can we avoid Join meeting buttons when the room is booked without a Teams or Starleaf or other videoconference link ?
Thank you,
Michel
That is behavior of the Cisco endpoint itself and the OTD service cannot change that.
Hi Jeff,
We have this setup. It works when one of our internal users creates the meeting with our Poly video conferencing unit.
However when an external user (not part of our company setup) sets up a meeting with our Poly video conferencing unit, the call fails, even if we do see a “join” button.
Is this supposed to work with users who have a standard teams invite and are without interop capabilities?
No, Cloud Video Interop only works with a Team meeting scheduled by users from a tenant that subscribes to a CVI service and thus includes the video conferencing details in the invitation.
Hi Jeff,
exactly, but why then create a Join meeting button on the device touchscreen ?
We have the same issue: when our meeting room is booked for a local meeting, without Teams/Realconnect, there is a light green Join meeting button, not functional, but creating confusion for the users. Why push a Join meeting button in this case ?
Moreover, in the OTD selection screen, we just selected Teams Webex and Starleaf, not anything else. Our understanding is that OTD should ignore all other meetings (with Zoom, Skype, Google Meet, Amazon Chime, etc., and … no videoconference at all)
Can you explain (and file a feature request to filter out these use cases if need be ?)
Thank you !
One Touch Dial is only processing the meeting invite, it’s the endpoint that actually parses the invite to generate a Join button. Even if OTD does not process certain meeting types, or if hte invite does not include anything to process the endpoint itself may still display a Join button based on it’s own behavior. For example if the video system sees a meeting invitation which does not include instructions provided by OTD (via a “VMR token”) then it’ll attempt to find other ‘callable’ information in the invitation itself, like a phone number or standards-based VMR ID. This can result in a Join button appearing but call attempt is not a valid destination.
Hi is OTD cloud is free for polycom cusotmers?
Yes, it’s free for use with Poly products. You’ll still need to ‘purchase’ a $0 license first though in order for Poly to allow your tenant to use the service.