As of the 8.1 firmware release of Polycom RealPresence Collaboration Server (RMX) SSL certificates are now managed using a completely different method than used with previous versions (7.6 and older).
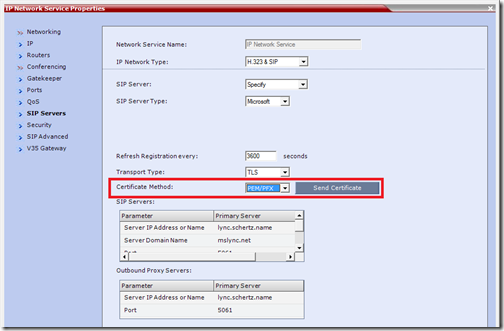
When integrating an RMX with Lync Server an SSL certificate must be issued to and installed on the RMX so that secure MTLS communications with the Lync Servers is possible. In older firmware versions the Certificate Method option was located in the SIP Servers settings window under the IP Network Services properties and provided the ability to import either a package of certificates (.PFX) or individual certificate files (.PEM), as well as directly issue new requests
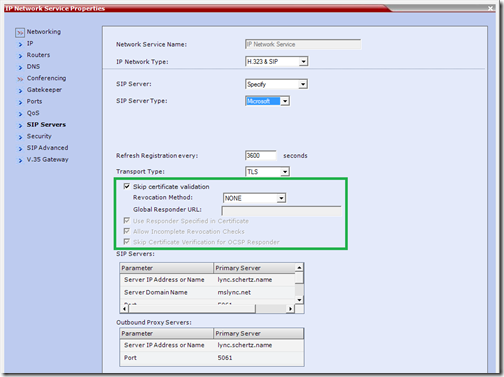
But when viewing the same properties window using RMX Manager 8.1 what is immediately noticeable is that the Certificate Method option is missing and in its place are a group of new certificate validation options.
This is clearly by design, as the RMX now utilizes a separate menu for managing all certificates. For each IP Network Service object in the RMX it is now possible to control these new Certificate Revocation features, but for requesting, importing, and generally managing the certificates themselves the Certification Repository menu now handles this.
Importing Certificates
This method is the most common approach when dealing with Lync Server integration as the official Polycom integration guide shows how to use Internet Information Server Manager to create a simple online certificate request against a Windows Enterprise CA.
The same instructions as documented for previous RMX versions would still be followed, but with two important changes:
- The certPassword.txt file is no longer used. That step in the official documentation can be ignored from this point on as the import process has been simplified to prompt for the PFX password directly.
- The PFX package is not imported on the SIP Servers properties window but in the Personal Certificate Repository menu.
- Following the Polycom UC Deployment Guide for Microsoft create a new certificate request using IIS Manager, issue the request to the Enterprise Windows CA, and then export the certificate, private key, and root CA certificate to a PFX file as instructed.
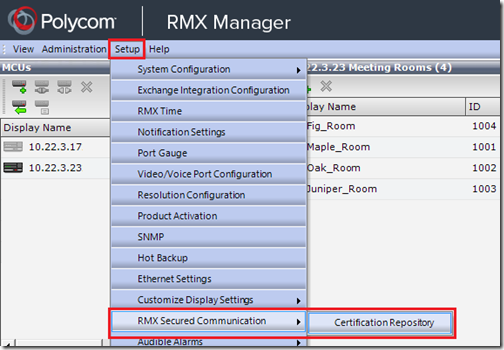
- Using the RMX Manager 8.1 (or newer) connect to an RMX also running firmware version 8.1 (or newer) and browse to the Setup > RMX Secured Communication > Certification Repository menu.
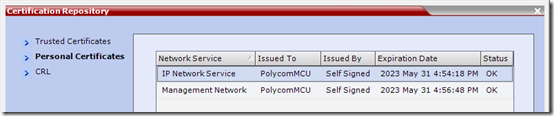
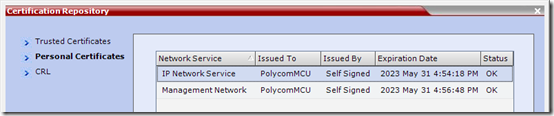
- Highlight Personal Certificates and verify the existing certificates. If the RMX is configured with factory defaults then a self-signed certificate would be listed here as assigned to each interface.
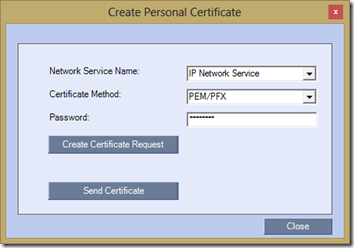
- Click the Add button to open the Create Personal Certificate window and change the Certificate Method to PEM/PFX. Enter the Password which was used to protect the PFX package and then click Send Certificate.
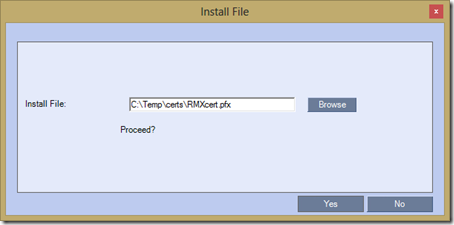
- In the Install File window browse to the previously exported PFX certificate package and click Yes to upload the certificate, private key, and CA chain into the RMX.
If successful the response should be “Message file transferred successfully” and RMX Manager will request to reboot the RMX to apply the new certificate to the SIP services.
Requesting Certificates
This method is seldom used when integrating with Lync Server, especially when a private Certificate Authority is used to issue SSL certificates as covered in the previous section. Yet when submitting requests to a public CA then creating the request directly on the RMX is a viable alternative method.
- Using the RMX Manager 8.1 (or newer) connect to an RMX also running firmware version 8.1 (or newer) and browse to the Setup > RMX Secured Communication > Certification Repository menu.
- Highlight Personal Certificates and verify the existing certificates. If the RMX is configured with factory defaults then a self-signed certificate would be listed here as assigned to each interface.
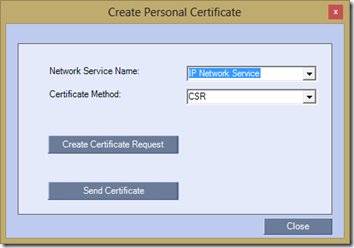
- Click the Add button to open the Create Personal Certificate window.
-
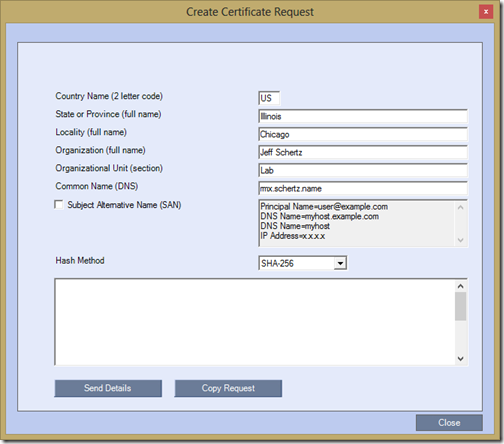
Select IP Network Services for the Network Service Name and then click the Create Certificate button to open the following Create Certificate Request window and then fill out the details as appropriate for the certificate’s needs.
In the scenario of integrating an RMX with Lync Server populate the Common Name (DNS) field using the Fully Qualified Domain Name previously defined for the RMX’s signaling interface (e.g. rmx.schertz.name). Leave the Subject Alternative Name (SAN) field unchecked as no SAN entries are used. For the Hash Method either SHA-1 or SHA-256 can be selected as both the RMX and Lync Server support each method.
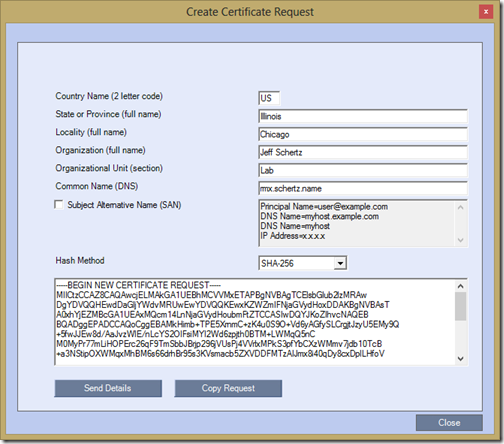
- When the form is completed click the Send Details button to create the certificate request text. Then click Copy Request to send the request data to the clipboard.
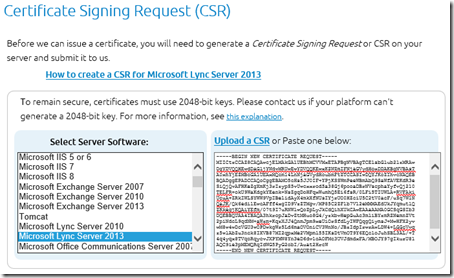
- Paste the data into a new text file (and save) or paste the string directly into the appropriate web interface or certificate management tool to submit the request to the Certificate Authority of choice.
In this example the certificate request was submitted to DigiCert and the response was received shortly after the domain used in the Common Name field was validated by them. Depending on the CA the response may come in the form of an individual certificate file (e.g. .CER) or a package (.PFX) containing the issued certificate as well as the certificate chain of any issuing and/or root CA servers. In either case the individual requested certificate needs to be separated and accessed in a Base 64 format which can be viewed in plain text and copied to the clipboard.
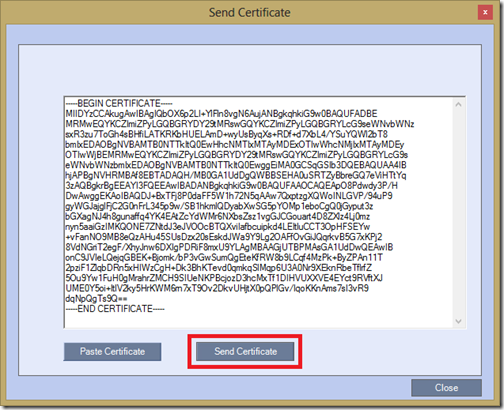
- Click Close on the previous window in the RMX Manager to return to the Create Personal Certificate menu.
- Click Send Certificate to open the Send Certificate window. Copy the issued certificate text to the clipboard (not the certificate request data created earlier, that will not work) and paste into this window.
- Click the Send Certificate button to complete the process and import the certificate into the RMX, replacing the self-signed certificate in this example.
At this point RMX Manager will request to reboot the RMX to apply the new certificate to the SIP services.
[…] http://blog.schertz.name/2013/10/improved-rmx-certificate-management/ […]
Awesome. Now they need to make certificates on DMA super-clusters a bit easier.
SSL Certificate management on Super-clusters is actually very easy, but this topic is unfortunately not well understood. I do plan to write up an article explaining the two supported Super-cluster integration approaches and both of them utilize a single SAN entry across the enter cluster so it is very simple to manage.
Jeff. This is indeed good improvement in the RealPresence Collaboration Server configuration. I have one question. I have RMX v 7.6 currently integrated with my Lync 2010. We have setup a parrallel Lync 2013 environment with different set of servers. I plan to upgrade my RMX to v 8.1 as indicated in your post (to be able to support Lync 2013). I want to know if i can have my RMX talk to both my Lync 2010 and Lync 2013? I want the users of both Lync 2010 and Lync 2013 to be able to make video calls to my RMX. How do I achieve this?
This will work automatically if both servers are part of the same topology. Do make sure and delete and recreate the application pool configuration in Lync to point to eh new 2013 registrar prior to decommissioning the 2010 servers.
Thanks Jeff. What if i am using multiple SIP? My lync2010 is on SIP1 and my Lync2013 is on SIP2. In such a case, for the Polycom RMX ICE configuration, i need to specify a domain account whose SIP should match by Parent Domain Name. In such a case, which pool should i make this domain account a member of so that my Lync 2010 and Lync 2013 users both can make Video Calls to Polycom from External Network?
You should only be pointing to the Lync 2013 server, you cannot leverage multiple servers. Because they are in the same topology that is sufficient for all users in all pools to be able to route calls to the RMX.
Could you explain the difference between the IP Network Service Cert, and the Management Network Cert?
I see you reference the IP Network Service on in this article. But I see the Management Service in you picture as well.
Only the IP Network Service is dealt with when setting up Lync integration. If you want to support HTTPS connections to the web management UI without getting an untrusted certificate alert in your browser then you can also apply an SSL certificate to the Management Service object, but this has no impact (and should not overlap or conflict with) the Lync configuration.
Can You explain what is SAN PrincipalName? Where it is used? Does it have to be unique in organisation? Why does it look like e-mail or SIP address? Does it have to be covered by real e-mail or SIP account?
The SAN is a contain which holds additional FQDNs for the certificate.
should the san include the real connect domain? Or just the IP network FQDN?
The RMX certificate should not include a SAN field, Common Name is all that is required, and it needs to match the DNS record setup for the IP Networking (Signaling) IP address.
Been working to integrate the PLCM platform with Lync2013, and found that our RMX did not like the internal CA certificates b/ it did not include the proper EKU values and issuer CN. After over a month of trouble shooting with PLCM this was discovered these were the issues.
We are now trying to determine why we are still getting errors on the RMX
1. SIP TLS: no response from Registration server (cs id1)
2. Can not establish connection with SIP registrar
3. Registration failed for some conference.
With the registration failed for some conference it’s important to note there are no active conferences; and none of the conference rooms are sip enabled.
I did however hear that SW 8.5 removes the requirement for a root CA to have an issuer CN. Likely the reason why it won’t currently accept our root cert.
Did upgrading to 8.5 resolve this issue?
Did you ever determine why registration fails for some conferences when SIP is not enabled?
We are having the same issues.
SIP must be enabled and configured properly on the RMX as part of the Lync/SfB integration.