The primary function of this article is to serve as a reference guide for submitting offline certificate requests against either a private Windows Enterprise Certificate Authority (CA) or various public third-party certificate authorities. When requesting certificates for servers, applications, or hardware devices most solutions work well when a commonly known certificate template is used to provide the X.509 certificate. Most Microsoft server applications (Lync specifically) by default will attempt to utilize the default Web Server template, but sometimes this template is not available.
It is becoming a common practice to harden an internal CA by disabling the default templates and duplicating them with customized names and settings. Often these changes may prevent proper operation of the intended solution, but if only something basic like the name was changed to “Contoso Web Server Cert” then the capabilities of the certificate may still be identical. Yet placing the request can become more complicated.
Additional roadblocks might be that the a different team controls all certificate requests in the environment and online requests are disabled. This usually requires that an offline request file is generated and sent to them for submission.
Over the years there have been multiple different approaches to generating and managing certificate request, and it seems each has it’s own caveats and limitations. A brief glance at any old documentation will show the familiar /certsrv IIS website hosted on a Windows CA, but this process is not as flexible and sometimes (depending on the Windows OS) can prevent advanced options like marking a private key for exportability within a given certificate. Then there is the CLI approach of using certreq.exe with inherent user-unfriendliness as many command-line tools do. The most common approach is usually to open the MMC and add the Certificates snap-in, which has a few pitfalls to trip up novices as well.
With the introduction of the updated Internet Information Services (IIS) Manager in Windows Server 2008 (inetmgr.exe) there is actually a very quick, easy, and repeatable method available to handling the majority of certificate request duties. The Server Certificates section contains a few wizards for performing online and offline requests, as well as basic exports of the certificate packages for moving into other systems. The various wizards also offer options for customizing the requests which may need specific key bit lengths, Subject Alternative Name entries, or be applied against a specific CA or template.
Online Request Process
The simplest process is a basic online request which will contact the Windows CA directly through the network to issue the request data. The generated private key stays on the requesting server at all times, and then CA will immediately return an approved certificate file back to the requesting server, which in turn automatically imports it in to the correct store and attaches the private key to it. If anything specific to the environment prevents this process (e.g. network access to the CA, insufficient permissions to perform requests, disabled ‘Web Server’ template, etc.) then skip to the Offline Request section of this article.
- From a domain-connected Windows 2008 Server launch the Internet Information Services (IIS) Manager (inetmgr.exe) and in the Connections window pane highlight the server object.
- In the main window (focused to Features View) open the Server Certificates feature under the IIS section.
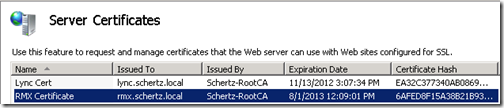
The main window pane will now show a list of all Personal certificates installed on the local server. (These are the same objects that appear in the Certificates MMC snap-in under the “Local Computer\Personal” store.)
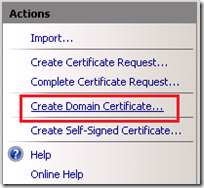
- From the Action pane of Internet Information Services (IIS) Manager select Create Domain Certificate which will launch a wizard to request, issue, and import a new server certificate all in one pass.
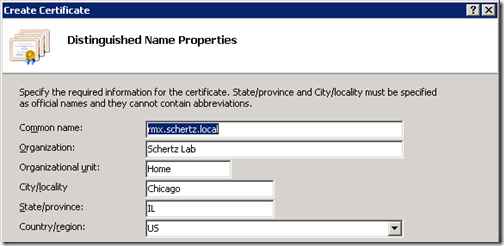
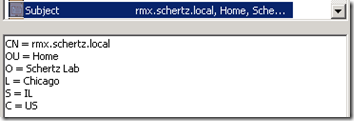
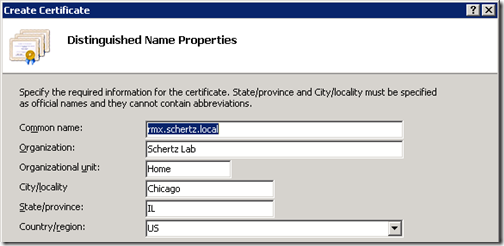
- In the Distinguished Properties window of the Create Certificate wizard enter the desired information in each field. The Common Name field is most important as this is the identity the server or application presents to remote hosts when attempting to establish secure communications.
As a best practice it is always recommended to fill out each of the identity fields so that the entire distinguished Subject Name field is formatted in a way that most applications expect to see it. Do not leave any of the fields blank; it is also a good idea to refrain from special characters or other non-alphanumeric digits when at all possible.
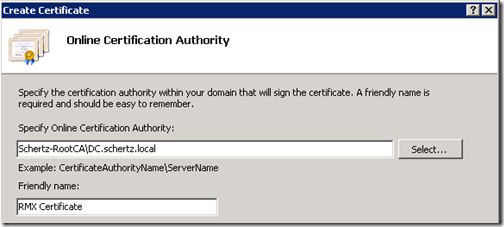
- In the Online Certification Authority window browse for the desired internal CA and then enter a Friendly Name.
- Click Finish and if successful the new certificate will almost immediately appear in the server list.
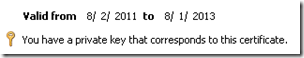
View the certificate details and validate that the private key was successfully assigned to the certificate.
Reviewing the certificate details shows the Subject Name, key bit length, and certificate template used.
Offline Request Process
In the event that a different key bit length needs to be requested or a custom certificate template must be designated then these can be addressed by submitting an offline request which breaks up the previously shown process into three separate manual steps: request, submission, and completion.
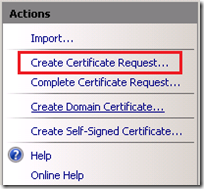
Create Certificate Request
- From the Action pane of Internet Information Services (IIS) Manager select Create Certificate Request which will launch a wizard to create a request and save the contents to a text file.
- In the Distinguished Properties window of the Request Certificate wizard enter the desired information in each field. The Common Name field is most important as this is the identity the server or application presents to remote hosts when attempting to establish secure communications.
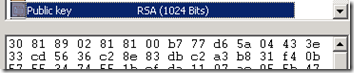
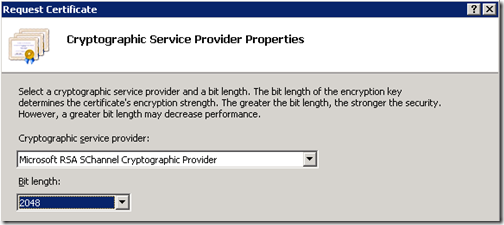
- In the Cryptographic Server Provider Properties window select the desired options. Rarely will a setting other than the Microsoft RSA SChannel option be selected, but it is becoming more common to increase the bit length above the default 1024 value. Many public CAs are no longer issuing certificates for requests generated with a 1K bit length, so moving up to more secure 2048-bit requests are more common-place.
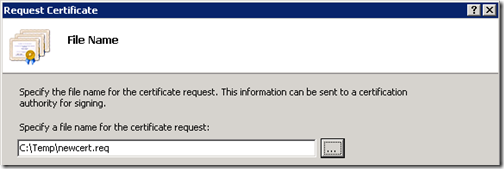
- In the File Name window enter a path and name for where the request file should be saved on the local server. Common file extensions are either .txt or .req and either can be used interchangeably.
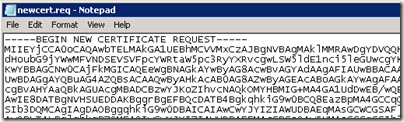
To verify that the data was correctly written to the file open it up with Notepad and the text should look something like the image below.
Submit Certificate Request
For requests submitted to a public CA simply copy/paste the text from the generated file to that CA’s request form and then wait for the completed .cer file to be sent back and then skip to the next section
But for internal requests there are multiple ways to submit them to a Windows CA. Depending on the tools and permissions available some of these approaches may not work in certain environments. If access is prevented for certificate submissions then send the request text file to the appropriate personnel and wait for them to send back the certificate file, then jump to the next section to complete the request.
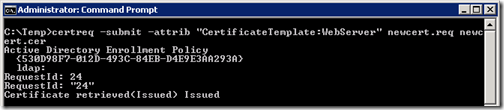
Assuming that both connectivity to the CA and the appropriate permissions are available then follow these basic steps to submit the request to the Windows CA using certreq.exe from the standard Windows command prompt.
- From the same server open the standard Windows Command Prompt. (If network connectivity to the CA is not available from this host then copy the request file to the CA server or anther Windows server with access and run these commands from that system.)
- Change to the current directory where the new request file was saved (e.g. C:\Temp) and issue the following command:
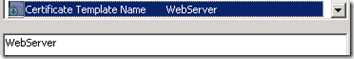
certreq.exe -submit -attrib "CertificateTemplate:WebServer" newcert.req newcert.cer
The CertificateTemplate attribute can be used to supply the name of whatever the custom template’s name is in the CA, assuming that template was configured in a way that is still compatible with the type of request generated.
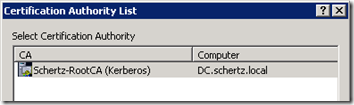
- In the Certification Authority List pop-up window select the desired Windows CA to submit the request against.
The results of the command should indicate a successful request and the resulting certificate file will be written to a new text file in the same directory as indicated in the command (newcert.cer).
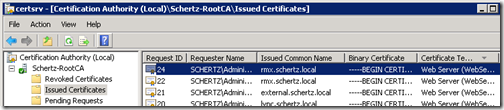
As the Request ID is displayed in the output above, then the details of the issued certificate can be verified on the CA itself by opening the Certificate Authority administrative tool on the CA server and then browsing to the Issued Certificates container to look for the matching ID.
Complete Certificate Request
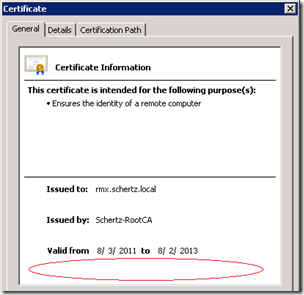
Before completing the request locate and open the newly generated certificate file (newcert.cer). Notice that the private key description is missing from the General tab information.
Although this appears to look like a ‘certificate’ file it is actually just the public key portion that is generated by the CA, the all-important private key portion is still stored locally on the requesting server and the two items need to be joined together to create an actual functioning certificate pair. Without a valid private key nothing can be decrypted which was encrypted using the public key.
Although this appears to look like a ‘certificate’ file it is actually just the public key portion that is generated by the CA, the all-important private key portion is still stored locally on the requesting server and the two items need to be joined together to create an actual functioning certificate pair. Without a valid private key nothing can be decrypted which was encrypted using the public key.
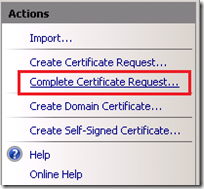
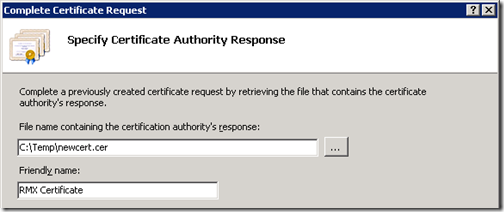
- From the Action pane of Internet Information Services (IIS) Manager select Complete Certificate Request.
- In the Specify Certificate Authority Response window browse for and select the certificate file (newcert.cer) and provide a Friendly Name for the certificate, then complete the wizard.
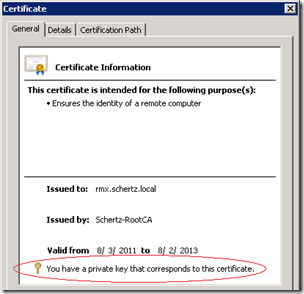
View the properties of the new certificate and this time the General information will indicate that the private key has successfully been linked to the new certificate.

Has been concerned about your Blog!
Thanks, but I have just been busy at work 🙂
Thanks! Incredible good post as always.
[…] the directions outlined in this previous blog article submit a new online certificate request against a Windows Enterprise CA using Internet Information […]
[…] Windows Server 2008 September 10, 2011 robertrieglerwien Leave a comment Go to comments http://blog.schertz.name/2011/08/certificate-requests-in-windows-server-2008/ Share this:PrintEmailLike this:LikeBe the first to like this post. Categories: MS: AD, Group […]
[…] approach is still to use the built-in Internet Information Services Manager as documented in this previous article. But this approach is limited in what options can be modified so when dealing with Subject […]
If a valid cert is requested from IIS to a CA and returned to IIS on the Lync server can Lync take advantage of it or do you have to use Lync to request certs?
Correct, as long as the certificate is requested with the proper fields and parameters. I normally shy away from using the IIS certsrv procedure as it is a little clunky and I find that using inetmgr for most requests is the least problematic.
jeff,
how can the cert can be more year? beside 2 year as default thanks
Jeff, how I can find the "CA’s request form " so I can paste te certificate ??
Diego, that is entirely dependent on what CA service is used. Generally these are just a web page in which you submit the certificate text.
[…] across the blog of Jeff Schertz. I’ve been to his blog before and always find great content. Here’s the referenced post but check out some of his other great articles; specifically for […]
Hi Jeff,
You've mentioned about limitation for "exportability within a given certificate". Currently I'm having problem with exporting EV Multi-Domain SSL certificate issued on IIS7 Win 2008 R2 and I cant export that key. Is this because of my OS?
Regards
Most likely the original request was not created with the ability to export the private key, so you'd have to create a new request for a new certificate.
you saved my day – thank you very much!!
[…] I requested certificates via UI with a local DC/ CA. This was after I found the article on how to import certificates using powershell. The code I […]