This article is intended for those following along with this series of deployment articles to create a Skype for Business (SfB) 2015 Server environment.
The instruction in this article is without much of the typical in-depth explanation provided alongside most deployment articles on this blog. A much more detailed companion article entitled Skype for Business 2015 Edge Pool Deployment is also available which overlaps with a lot of the concepts and steps in this article. This other article addresses the more complex topic of deploying multiple Edge servers in production-like setting, but also includes additional guidance and can be used as a deeper reference to the topics covered in this shorter article. Basically the other servers as a production deployment reference guide while this is the quick reference guide for lab deployments. Nearly all of the guidance in the companion article related to network configuration and server preparation holds true for either scenario.
Also worth pointing out is that if one is attempting this deployment then a fair amount of Windows server and networking knowledge is assumed. Because the Edge Pool article goes into great depth on topics and step-by-step directions this article will omit some of the basic instructions on how to get to specific windows and focus on just the important aspects.
Preparation
The baseline for this deployment is a new Windows Server 2012 R2 installation that is not joined to any Active Directory domain and is connected to two separate IPv4 networks. These are basic requirements for an Edge Server and must be met in order to move forward with a successful deployment.
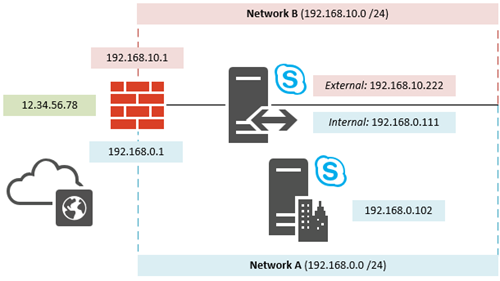
The network topology of the lab environment used for all the articles in this deployment series simply consistent of two physically separated network segments.
A single firewall with separate network interfaces provides connectivity for each network segment to the Internet. The two networks do not have access to each other except for any explicitly defined firewall rules. The rules required to allow communications to and from the Edge Server across either network are covered in the Edge Pool article which can be used as a reference. Make sure to open and test the required ports and protocols before attempting to deploy and start the Edge Server services.
Configure Network Interfaces
The existing server has been prepared with two network interfaces connected to two separate IPv4 networks.
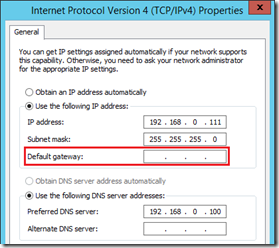
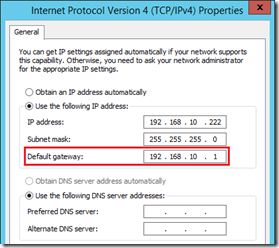
In order to allow normal communications typically the internal interface would have been configured with the default gateway set to the router’s IP address for that segment and the external interface would not yet have a default gateway set.
The server cannot have multiple default gateways defined yet moving the server’s default gateway to the external interface might break communications with hosts on other routed internal networks than the one it is directly connected to. To prevent this problem then some persistent static routes are required. This topic is covered in more detail in the Edge Pool deployment article which outlines creating up to three new persistent static routes to tell the server to use the internal router to locate hosts on any of these reserved IP address ranges. This is a normal practice in environments with multiple routed internal networks but unnecessary in a standalone lab environment like what is used in this example.
- Review the current IPv4 configuration on both the Internal and External interfaces and configure the default gateways as appropriate.
If Remote Desktop connectivity is lost after moving the default gateways as shown above then connect to the server console and either define a required static route to back to the network where the remote console is, or if that console is actually in the ‘External’ network then check the firewall configuration to allow remote desktop connections to the external interface. Clearly this is safe in a lab environment but if the Edge server’s external interface is to be routed to the Internet than a different approach may be advisable.
Configure Computer Name
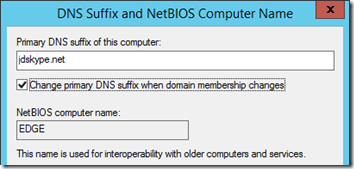
As covered in the other article it is critical to set the proper Fully Qualified Domain Name (FQDN) on this server so that the server component installation will function correctly. This is a commonly missed step that leads to troubleshooting installation issues further down the line.
- View the server’s System Properties and use the More button under Computer name field to access the following window. Enter the same DNS domain and suffix used by the internal SfB Front End server so that the Edge Server is configured with an FQDN.
- Reboot the server to apply the new computer name.
Add Server Features
The Windows 2012 R2 operating system used on these servers already includes some of the require components by default (like PowerShell 3.0) and as the Edge server does not contain any web service components then IIS subcomponents will also not be installed on these servers.
- If the server does not have Internet connectivity then mount the Windows Server 2012 installation media on the server to an available drive letter as some of the components to be installed will need to be read from the installation media as provided by the Source parameter in the following cmdlet (e.g. D:\sources\sxs).
- Launch Windows PowerShell by selecting ‘Run As Administrator’ and enter the following cmdlet to quickly install the .NET Framework package, the Remote Server Administrative Tools, and all additional prerequisites followed immediately by a required server reboot. (The Telnet client is also installed as it helpful for testing/troubleshooting port connectivity issues with the Edge server.)
Add-WindowsFeature RSAT-ADDS, NET-Framework-Core, NET-Framework-45-Core, NET-Framework-45-ASPNET, Web-Net-Ext45, NET-WCF-HTTP-Activation45, Windows-Identity-Foundation, Telnet-Client –Source D:\sources\sxs
- Once the installation is complete a restart will not typically be required, but if prompted to do so then reboot before moving on to the next step.
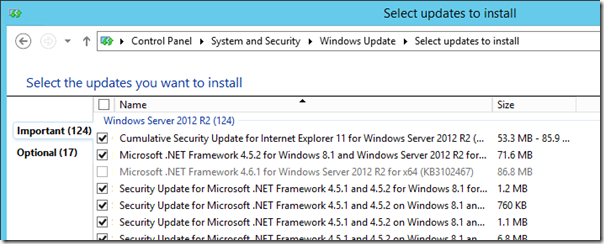
Windows Updates
Before installation any SfB components make sure to apply the most recent Windows Updates, with one notable exception: do not install the Microsoft .NET Framework 4.6.1 package as this is not currently supported by Microsoft.
- Run Windows Update and hide the package for Microsoft .NET Framework 4.6.1 for Windows Server 2012 R2 for x64 (KB3102467). Install any other pending recommended updates.
Configuration
This section covers updating the SfB Topology and access policies to enable both the deployment of the Edge Server and enable its functionality.
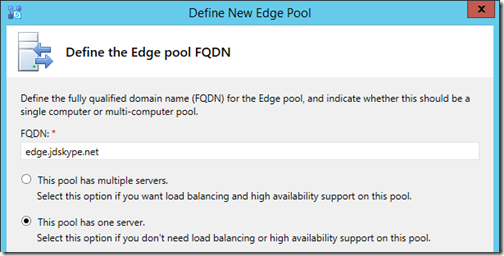
Define Edge Pool
- Open the Skype for Business Server Topology Builder tool on the existing SfB Front End server, then download and save the current topology to a text file.
- Navigate to the desired site, expand the Skype for Business 2015 container, highlight Edge Pools and then select the New Edge Pool action.
- Enter the desired Pool FQDN (e.g. edge.jdskype.net) and then select the option for This pool has one server.
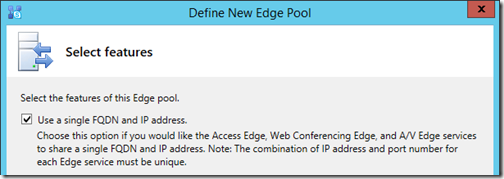
- On the Enable Federation window select the desired options, in this case only the Enable Federation option is addressed. The Skype Search and XMPP options can be enabled now or later if so desired.
- Select the option to Use a single FQDN and IP address.
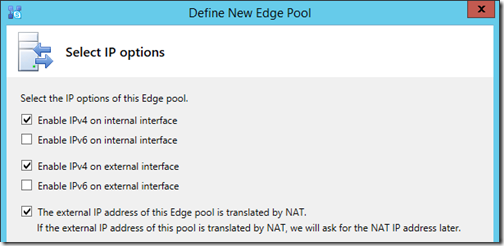
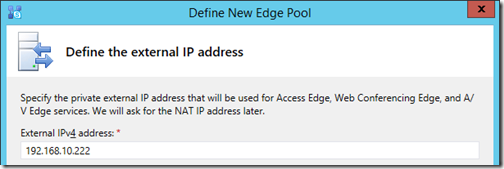
- For this deployment only IPv4 addresses will be utilized, and for any Internet access then Network Address Translation (NAT) will need to be used as the Edge server’s external interface has a private IP address bound directly to it.
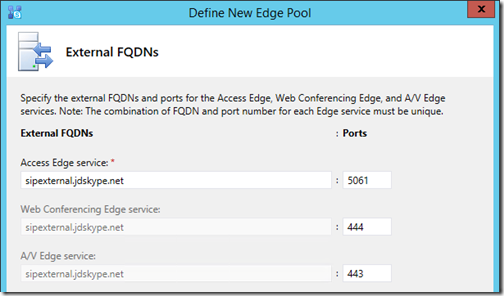
- In the External FQDNs window the wizard will populate the suggested ports due to selecting the single FQDN and IP address option earlier.
Leave the suggested ports as these are typically the best options available. The Access Edge service will collocate external client and federation traffic on the same port (5061) and it is recommended to leave 443 assigned to the critical A/V Edge role to provide the best chance of successfully negotiating media sessions. The assigned FQDN is typically “sip.<sipdomain>” but in this lab environment a different FQDN is used to avoid potential overlap with the internal sip record. While any name can be used the sipexternal FQDN is one of the legacy Host (A) look records used by many clients and IP phones, so it was selected for that reason primarily.
- At the Define the computers in this pool window click Add to launch the Add server to Edge pool wizard.
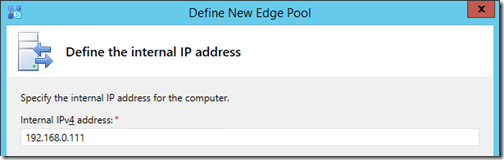
- Enter the Internal IPv4 address that is assigned to the internal interface.
- Enter the External IPv4 address in the proper field for each service and then click Finish.
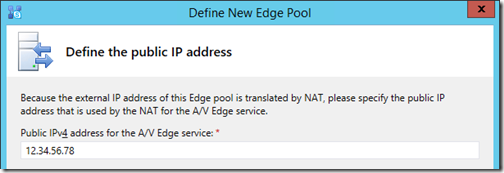
- Enter the Public IPv4 address for the A/V Edge service which will be translated to the server’s actual external IP address. This NAT configuration would be handled by the firewall depicted in the original diagram and is not addressed in this article.
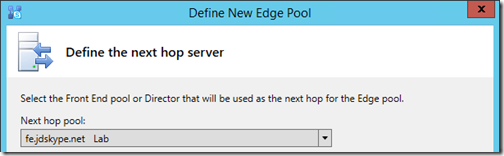
- Select the desired Next hop pool from the drop-down menu (e.g. fe.jdskype.net).
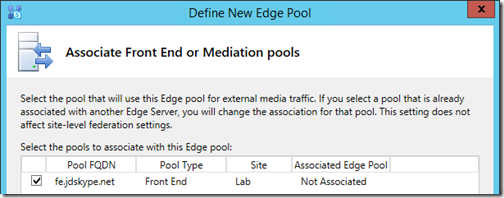
- At the Associate Front End or Mediation Pools step select the desired Front End server or pool, which in most cases is the same as what was just selected in the previous step (e.g. fe.jdskype.net).
Publish Topology
Now that the new pool has been created the next step is to save and publish these changes to the Central Management Store.
- In Topology Builder expand the newly created Edge Pool and double-check the configuration on the pool and each computer object to make sure there are no mistakes.
- From the Action menu select Topology > Publish to launch the Publish Topology wizard. If all goes as planned then the result should be reported as successful on all steps.
Enable External Access
While the majority of the environment preparation is handled in the topology this is a critical step which must be performed before any external communications will be allowed. The three major types of communications supported by the Access Edge service are Remote User Access, Federated User Access, and Public Provider Access. To enable one or more of these feature follow these example steps.
Only remote user access will be enabled in this article. For reference the Edge Pool deployment article discusses the other external communication types.
- Using the Skype for Business Server Control Panel browse to the Federation and External Access section
- Under the External Access Policy page open the default Global policy and check the Enable communications with remote users option and save the changes to the policy.
-
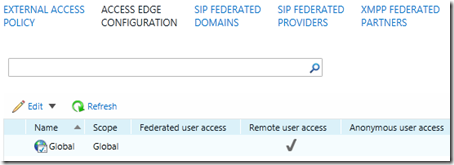
Under the Access Edge Configuration page open the default Global configuration and check the Enable remote user access option and save the changes to the configuration.
Export Topology
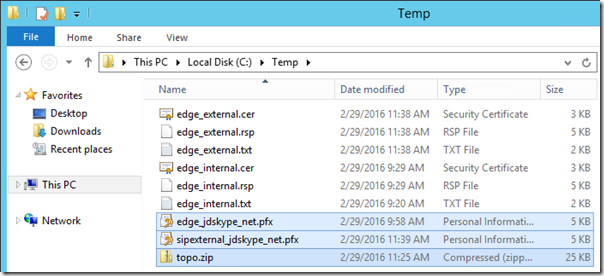
As briefly discussed earlier the Edge server deployment will require that the SfB topology data is manually exported and imported on the Edge servers which do not have the ability to locate and download this configuration information automatically.
- Using the Skype for Business Management Shell run the following Export-CsConfiguration cmdlet to export. (This file will be retrieved in a later deployment step.)
Export-CsConfiguration -FileName c:\temp\topo.zip
Deployment
Due to this being a lab installation then private certificates will be involved. Both the internal and external Edge certificates will be issued from the same AD-integrated Enterprise Certificate Authority (CA) that was used for certificates assigned to the other SfB server roles. If a public certificate is intended to be used on the external interface then the other article covers those configuration steps.
Full step-by-step directions for performing these actions can be found throughout a myriad of other articles covering various options like using the SfB Certificate Wizard, Internet Information Services Manager, the Windows certificate snap-in and even third party tools. For the steps outlined below the popular, free DigiCert Certificate Utility for Windows is utilized.
Create Internal Certificate
Because the SfB Front End server is joined to the domain then it is an ideal host to perform online certificate requests to the AD-integrated Enterprise CA.
- Download, install and launch the DigiCert tool on the SfB Front End server.
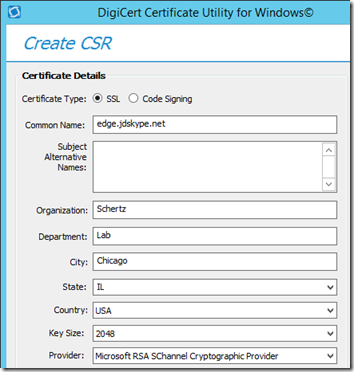
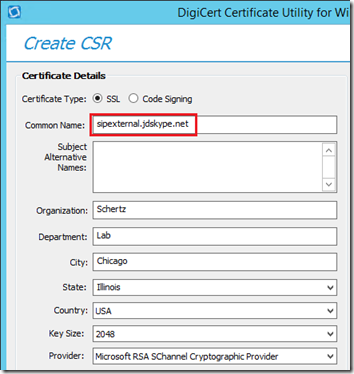
- Fill out the Certificate Details field as appropriate for the Edge Server Internal certificate. The Common Name field should be the FQDN of the Edge Server (e.g. edge.jdskype.net) and the Subject Alternative Name (SAN) should be blank.
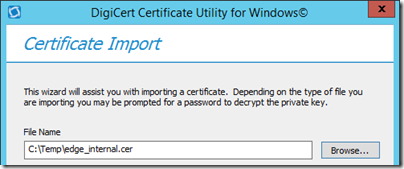
- Generate the request and then save the request data to a text file on the local server (e.g. C:\Temp\edge_internal.txt).
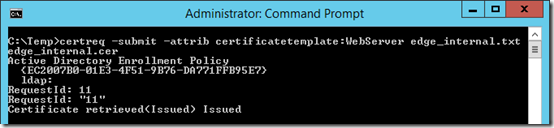
- On the same Front End server launch either the Windows Command Prompt or PowerShell as an administrator and then issue the following certreq.exe command. Supply the name of the text file saved in the previous step which contains the certificate request information and then enter the name of the new certificate file itself to be created (e.g. edge_internal.cer).
certreq -submit -attrib certificatetemplate:WebServer edge_internal.txt edge_internal.cer
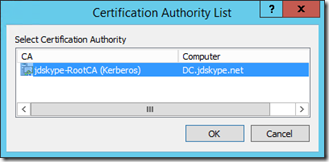
- When prompted to select a Certificate Authority highlight the desired CA (in this environment there is only a single Enterprise Root CA).
- Select OK and if the process is successful the end result should be reported as Issued.
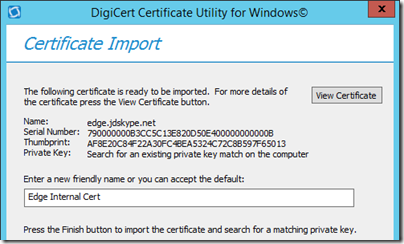
- Use the Import option in the certificate tool to import the issued certificate file (e.g. edge_internal.cer) into the server.
- Enter a descriptive Friendly Name (e.g. Edge Internal Cert) to complete the certificate creation process.
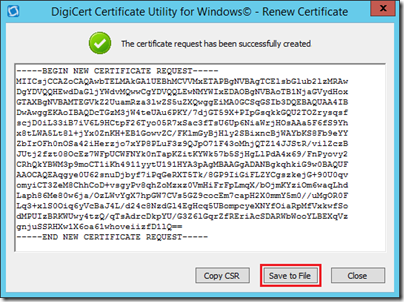
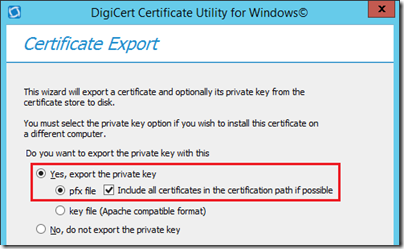
- Return to the main SSL window of the utility and highlight the newly imported certificate (e.g. edge.jdskype.net) and then click Export Certificate.
- Make sure to select the options to Export the Private Key and to Include all certificates in the certification path.
These options are critical as without the private key this certificate is useless to the Edge server. Also the issuing Root CA’s public key needs to be manually imported into the Edge server because it is not a member of the AD domain and has not automatically been provided these root certificates. These options will address both of those requirements.
- Define a password (e.g. password) to protect the export file which will contain the certificate’s private key. This step is mandatory and cannot be skipped.
- Choose a location and filename to save the exported certificate (e.g. C:\Temp\edge_jdskype_net.pfx). (This file will be retrieved in a later deployment step.)
Create External Certificate
Now that the internal certificate for the Edge Server is ready a second certificate needs to be created for the external interface. Typically this request is sent to a third-party Certificate Authority and the process above can be used to do that. Instead of running the certreq.exe command simple copy/paste the request text into the request field of whatever CA is used.
- Repeat all the steps above in this section to request, import, and then export the Edge Server external certificate. The only configuration difference is that the Common Name will need to be set to the Edge Server’ External FQDN that was defined (e.g. sipexternal_jdskype_net.pfx).
Now that all the server and environment preparation steps have been completed then the final processes of actually installing and configuring the Edge Server roles can begin.
Copy Files
The exported files created in the previous certificate topology and certificate preparation steps need to be manually copied from the Front End server to the Edge server.
- On the SfB Front End server locate the topology export file (e.g. C:\Temp\topo.zip) and the two exported certificate packages (e.g. C:\Temp\edge_jdskype_net.pfx & C:\Temp\sipexternal_jdskype_net.pfx).
- Copy these three files to the Edge Server to prepare for deployment and configuration steps in the next section.
Install Server Components
The steps in this section address the installation of the actual SfB Server components using the deployment wizard. These steps can be performed on both servers simultaneously or one after another.
- Mount the Skype for Business Server 2015 installation media on the first Edge server and then open the mounted drive to trigger autoplay of the deployment wizard.
The deployment wizard will automatically (if needed) install Visual C++ 2013.
- When that package installation is complete then select the option at the next window to skip checking for any updates. Leave the default Installation Location. Click Install to advance.
- Accept the licensing agreement and then wait while the deployment wizard automatically installs the Core Components.
- Once the main screen appears select the option to Install or Update Skype for Business Server System.
- On the Install or update member system window click Run on Step 1: Install Local Configuration Store.
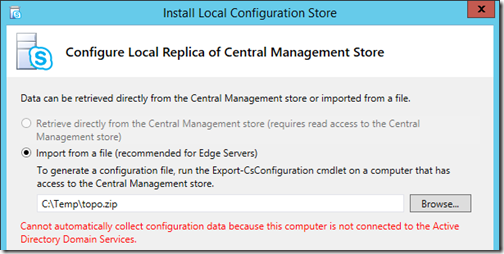
- The next window will be limited to a single option because this server is not a member of any Active Directory domain. Browse to the location where the exported topology file (e.g. topo.zip) was copied to in the previous section and click Next.
The local configuration store installation process will begin immediately by loading the local installation files and then performing a check against the various prerequisite components currently installed on the server. Assuming none of the prerequisites are missing and no problems occur with the installation of the SQL Express components then after some time that Task Status should be reported as Completed.
- Return to the Install or update member system window and click Run on Step 2: Setup or Remove for Business Server Components.
This concludes the server components installation process and all that remains is to import and assign the SSL certificates before the individual services can be started and tested.
Assign Certificates
The separate internal and external certificates that were created earlier in this article can now easily be imported into the server and assigned to the proper roles.
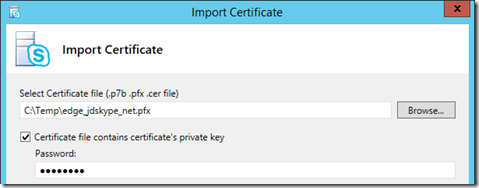
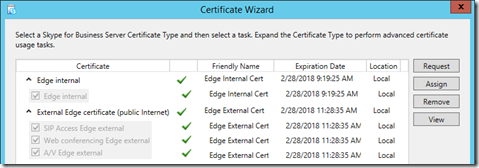
- Click Run on Step 3: Request, Install, or Assign Certificates to launch the Certificate Wizard.
- Click the Import Certificate button and then enter the location of and the password for the export file which was already copied to the Edge server in an earlier section.
- On the Import Certificate Summary page confirm that the Contains Private Key value is displayed as True, indicating that the import file is a complete certificate, and then click Next to complete the process.
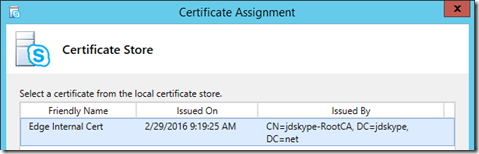
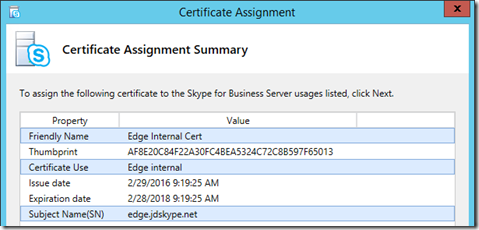
- On the Certificate Wizard home page highlight the Edge internal row and click Assign.
- Select the desired certificate (e.g. Edge Internal Cert) and click Next.
- On the summary page verify that the desired Certificate Use matches up with the correct certificate as identified by the Friendly Name and Subject Name fields.
- Finish the wizard to assign the certificate to the internal Edge service.
- Repeat all steps above in this section, but this time select the External Edge certificate.
The Certificate Wizard should now indicate that the chosen certificates have been assigned to the appropriate roles, as indicated by the green checkmarks.
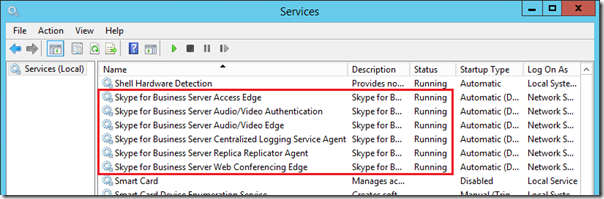
Start Services
The final step is to start the SfB Edge Server services. The new Start-CsPool cmdlet provided in SfB Server 2015 only applies to Front End pools and cannot be used with Edge Servers. Thus the services can either be started manually or the server can be rebooted to leverage the automatic startup procedure.
- Restart the Edge server and when it comes back online monitor the status of the individual services to validate that all have started successfully.
![image_thumb[102] image_thumb[102]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb102_thumb.png)
![image_thumb[69] image_thumb[69]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb69_thumb1.png)
![image_thumb[84] image_thumb[84]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb84_thumb1.png)
![image_thumb[86] image_thumb[86]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb86_thumb.png)
![image_thumb[90] image_thumb[90]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb90_thumb1.png)
![image_thumb[93] image_thumb[93]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb93_thumb1.png)
![image_thumb[95] image_thumb[95]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb95_thumb1.png)
![image_thumb[104] image_thumb[104]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb104_thumb1.png)
![image_thumb[114] image_thumb[114]](http://blog.schertz.name/wp-content/uploads/2016/02/image_thumb114_thumb1.png)
Hi Jeff, just as a note, there is a 404 on the Skype for Business 2015 Edge Pool Deployment (http://blog.schertz.name/2016/02/skype-for-business-2015-edge-pool-deployment) link in the first paragraph, which should be http://blog.schertz.name/2016/03/skype-for-business-2015-edge-pool-deployment/ – note the 03 not 02:)
Otherwise, thanks you very much for the series.
Great article, Really enjoyed the reading
I have enjoyed your articles but keep running into an issue.
I am setting up Skype for Business 2015 Server Standard so all roles are on the same server.
I have setup a virtual machine with one NIC. It’s IP address is 10.0.10.44. It is behind a firewall. I have setup the appropriate firewall rules to NAT and allow the appropriate ports to that internal IP from an external x.x.x.x.
To the issue. To the ‘define the internal IP address’, I put in 10.0.10.44. Got it. ‘Define the external IP address’, which your article indicates is the internal IP address that the external is NAT’ed to, will not allow me to put in 10.0.10.44, stating it is already in use. If I put in x.x.x.x, it takes it, but doesn’t work.
‘define the public IP address’ takes x.x.x.x with no issue.
So… I guess the question is, do I just add another IP address to my server, let’s say 10.0.10.45 and use that?
The internal and external addresses cannot be the same network, so you need to connect the external interface to a different network. If that is also a private network then that address is NATed to the real public IP on the outside as well.
Hi,
You will need to do extra steps to get it working for “same subnet”.
https://uclobby.wordpress.com/2014/04/17/lync-edge-server-on-a-single-subnet/
Hello,
I have tried to implement edge server with single public ip and without RP and public certificate..
When i am trying to check the same from Lync connectivty anayalser i see it is pushing internal edge ssl certificate which has no San name..becasue of that my aceessedge fqdn deosnt matcches the ssl certificate and authentication gets fail..
any idea where i am going wrong
i am using accessedge fqdn :5061 port
Hey man!
Configuring the Web Application Proxy would be the same concept correct?
What I mean by that is Network card with two nics one on DMZ and one on Local network..
Howie
Yes, although this depends on the platform you would be using.
Jeff,
Would you do a blog post on the Groupseries/Skype and DMA integration w. Realpresence touch?
I have been able to get the external communication working! however I am getting the message” Analyzing the certificate chains for compatibility problems with versions of Windows.
Potential compatibility problems were identified with some versions of Windows.
Additional Details
The Microsoft Connectivity Analyzer can only validate the certificate chain using the Root Certificate Update functionality from Windows Update. Your certificate may not be trusted on Windows if the “Update Root Certificates” feature isn’t enabled.
Elapsed Time: 3 ms.”
Other than that everything passes without a problem! thanks for your threads!
hi if i dnt have public ip then how can configure for home lab test?
You would need to use Network Address Translation (NAT) which is covered in various other article found online.
Can you tell me with which program you make diagrams.
Maybe send me a template 🙂
Thanks
I simply use Visio for my diagrams and mspaint for editing most screenshots. Nothing fancy here 🙂
Hi
I am hosted server on my test environment, how can I connect Lync from another domain. When I am connecting Its showing error
Hi Jeff,
can you tell me what type of third party certificate should I use (multi-domain, basic, premium) in order to have all SfB functionality externally?
Thanks in advance !
The various CAs use different terminology but all you need is a standard SSL certificate, usually created for websites. Make sure to get a multiple-SAN certificate for the external Edge interface though, often referred to as ‘UC Certificates’.
Hi.
I have only 3 Services in the Service list on my Edge Server.
S4B xmpp-Gateway
S4B Cetralized Logging Service Agent
S4B Acces Edge
Ist that correct?
And i have the Problem, that i can Chat with an external 365 User but i cant make a call.
Thx.
Ali, there should be additional services listed so it appears that the installation may not have completed successfully.
Hello Jeff,
i have the same Problem. I did everything as you did and i have the 2 Services running. The Logging Service and the Access Edge Service. Can you maybe identify where the problem may occur where i have to change a setting maybe a port?
greetings
coyni
Hi,
I’m looking a 3rd party tool to prevent users to logout/exit from skype for business.
Hi,
The link in this article to your
Skype for Business 2015 Edge Pool Deployment article
is broken.
you put
http://blog.schertz.name/2016/02/skype-for-business-2015-edge-pool-deployment/
it is actually
http://blog.schertz.name/2016/03/skype-for-business-2015-edge-pool-deployment/
Cheers
Thanks, fixed.
Hey Jeff,
For external access to meet.**, is that made possible through the edge server or do I need a reverse proxy for this?
Found my answer, Jeff! Nice Blog none the less!
Hello, Jeff, I has big probelem with Skype Edge! Ist es richtig dass der Edge Server nich in der Microsoft Domäne ist? I have only taken over the system, however, nothing is described. Can you help me?
Many greetings
Andreas
Sorry,
is it right that the Edge server nich in the Microsoft domain is?
Hi Jeff,
These question may have been asked many a time but it not clear in TechNet so would like to post here.
Regarding the Internal certificate for a SfB Edge Pool with 2 servers – we know from the deployment wizard that the Subject Name will be the FQDN of the Edge pool that’s a given. What’s not clear in a Edge Pool scenario if the internal certificate needs to be the same on each server in the poo OR should we follow the same rule as the external certificate and export from one server and import to the other so that the certificate on each is the same.
Lastly what certificate is uses on the Edge to create the AV Authentication token. Is it the Internal or the external certificate?
How would one show which certificate is used in a WireShark trace or Snooper Log from a client.
Thanks, Nick
All Edge certificates should be the same exact cert. So you only request/issue a specific role certificate once, and then export/copy it to all other servers in the pool. That means the internal cert should be identical on all servers in the pool, and the external cert (a different cert) should also be identical between external internals on all servers.
The internal Edge cert is used for AV authentication as that service is only available on the internal interface. The MRAS process is performed between the internal Edge and the Front End servers. Also the AV FQDN should not be included on any certs.
I have a standard setup that I did following your step-by-step guide (great job you did here.)
I am running Skype for Business 2015 and the latest CU (Core Components/ Front End / Edge server = 6.0.9319.277)
I have 1 Front End , 1 Edge, 1 Reverse Proxy. The Edge has Internal and external NICs and the external one is using one public IP.
sipexternal.domain.com uses default ports (5061, 444, 443)
All the devices I’m testing are remote.
Calls from iPhone to iPhone (iOS 10.3.1) work.
From iPhone to desktop/Laptop (Windows 10) work.
But from desktop/laptop to iPhone does not work. When I stat the session it sends the first message to the IPhone, iPhone receives it , but the session breaks at this point, nothing can be sent from either side.
I’ve already checked firewall, DNS, certificates, etc. All looks OK. I ran the Microsoft Remote Connectivity Analyser and I get “Connectivity Test Successful with Warnings”
Warning details: The Microsoft Connectivity Analyzer can only validate the certificate chain using the Root Certificate Update functionality from Windows Update. Your certificate may not be trusted on Windows if the “Update Root Certificates” feature isn’t enabled
Any ideas?
Thank you in advance,
Hi Jeff,
all of the sudden I have errors on FE:
41024
No connectivity with one of the Web Conferencing Edge Servers
Edge Server Machine FQDN: edge.domain.com, Port:8057
41026
No connectivity with any of Web Conferencing Edge Servers. External Skype for Business clients cannot use Web Conferencing modality; Service may be unavailable or Network connectivity may have been compromised.
All services are working as it should and 8057 port is open and listening on Edge not being firewalled.
Should I have EDGE internal certificate present also on FE server?
Can you point me to resolution?
Thank you in advance
Your big follower 🙂
No, the Edge Server certificates do not need to be copied to any other servers.
Oh… forgot to mention that certificates were renewed more than a month ago, but those errors started to after update the latest OS patches and restart few days ago.
Hi Jeff
We have used port 5061 for Access Edge Service (Default port), now we want to enable federation. But Federation also want to use port 5061 on the external interface.
Can you advise how to go forward?
Thanks in advance.
You can either leave both Remote Access and Federation on 5061 or you can move Remote Access to 443. Either approach works as the Access Edge service can listen for both federation traffic and remote clients on the same port (TCP 5061).
Hi Jeff,
followed your Guide but cannot federate with any external SfB Users. Microsoft Remote Connectivity says all good.
What can i do?
Regards
Hi Jeff,
I just want to confirm the following when dealing with multiple SIP Domains.
For the primary domain we need a SIP edge and A/V and web conferencing edge URL but for the additional SIP domains we just need the SIP edge domain?
sip.contoso.com
access.contoso.com
access1.contoso.com
sip.abc.com
sip.def.com
sip.efg.com
That is the preferred approach. Defining a unique SIP FQDN for each SIP domain provides for seamless legacy client discovery and registration. It also helps with Open Federation.
Hi,
I have environment:
Front End Server working fine internally,however after deploy Edge Server i face issue while starting “Skype for business Access Edge Service” not started.
Service Error:
“Windows couldn’t start the Skype for business server access edge on local computer.For more Information review the system event log.If this is non-micro soft service contact service vendor and refer to service-specific error code -1008125707”
After review Event Logs :
Error Log1 :
The Protocol stack reported a critictal error : code 0xC3E93C62 (Configuration failure prevented the server from starting up). the service has to stop
Error Log 2:
The Protocol stack reported a critictal error : code 0xC3E938F5 (SIPPROXY_EVENT_EP_EXTERNALFQDN MISMATCH). the service has to stop
Error Log 3:
Access Edge server external edge FQDN cannot be located in the certificate configured for its external edge.
External FQDN : sip.domain.com.pk
Make sure the certificate configured on the external edge of Access Edge Server matches its external FQDN
Cause : The Skype for business server failed to initialize with configured certificate
Review and correct the certificate configuration, then start service again
What I need to check first please guide step by step
Need Support on urgent basis
Hello Jeff, Thanks for the great article. I’m running to a problem accessing from an external computer to SfB. (ex my home computer).
i have one edge pool configured (edge.domain.com) it has 4 NICs, one with my LAN IP, 3 with public IP addresses (one for access, one for webconf and one for av). I have assigned a public cert to my external edge (SAN: sip.domain.com and webconf.domain.com). I created a records for sip/webconf/av.domain.com on a public dns(i can ping them), i also created an A record for sip.domain.com on my internal dns pointing to front end pool IP and a srv record named _sipinternaltls pointing to sip.domain.com on port 5061.
I also enabled external access policy and access edge configuration for remote users.
But when i want to login to my sfb account there’s an error:
“couldn’t find a sfb server for domain.com, there might be an issue with dns config for your domain”
any help will be really appreciated.
hi
i have probkem.all step in edge server checked green but service access edge server can not start.what is problem?
Hi Jeff,
Thank you for your great sharing!
If set up the environment according to your guidance, do I need to import any certificate to my windows or MAC PC which I’m about to have S4B client login in out side?
Thank you in advance,
Jov
If you are using a trusted 3rd party certificate (e.g. GoDaddy) on the external Edge interface(s) then there is no need to import that root chain into any devices. But if you are using a private CA then you may need to import them, unless the devices are domain-joined and you are using an Enterprise CA which already has it’s root certs stored into Acitve Directory which automatically are pushed to domain members.
hi Jeff
I install and config my sfb on local domain like sfb.local and my internal clients insert they account with this format ex: test@sfb .local but my external dns is sfb.com , now my external client how can connect to skype?
You cannot use a .local suffix on a user’s SIP URI if you plan for them to connect externally via the Edge server. You need to use a externally-resolvable TLD like .com for your user accounts.
Hi Jeff,
I have deployed my Sfb environment using your steps by steps article.. all my servers is virtual machine hosted in Hyper-v.. As of now I have only 1 DC server, 1 standard edition FE, and 1 edge.. I dont have reverse proxy server yet.
My internal skype client is able to login to Skype but my external client cannot sign in.. for external edge certificate I use my private Windows CA and I have installed root CA certificate into my external client machine. I then manually configured skype client to point to my my access edge sipext.domain1.com… I have DNS record on Public DNS which point sipext.domain1.com to my edge server IP address .. But I get error message saying having trouble connecting to server when trying to sign in.. any advise on this? Is it possible for external desktop client to login skype without deploying reverse proxy? If I manually configured the skype client to point to access edge, do I need other external DNS record?
Thanks Jeff
It’s been a while but I think it may no longer be possible to use a private CA cert on an Edge server due additional certificate validation checks the clients perform, but I could be mixing this up with something else. I’d suggest reviewing public forums to see if anyone has attempted this in the past several years.
My Skype on the internal network is on an un valid domain. I also have a reputable domain on the Internet. I launched Skype edge , but because the internal users of my network are built with an unreliable domain, they cannot log on to the Internet via Skype edge.How to make a connection between an invalid domain and a valid domain ?
You cannot use an internal DNS namespace that is not part of a valid Top Level Domain (TLD) domain name space as your SIP domain and still support external or federated use. You need to change your user’s SIP URIs to use a valid domain name.
[…] Now we can deploy the Edge Server Rolehttp://blog.schertz.name/2016/03/skype-for-business-2015-edge-server-deployment/https://www.msxfaq.de/skype_for_business/lyncedge.htm […]
Hello Jeff
a question please.
i have a new edge vmware (10.49.66.61 network internal) in my pool edge ( this is the third, i ha ve other two edge that work fine) .
This New Edge don’t work,if i shutdown the two edge that work fine, and maintain only this edge , The Login don’t work.
i have verify with wireshark that is blocked in the third phase:
1306 2020-10-15 07:26:57,690614 10.49.64.195 10.49.66.61 STUN 256 Allocate Request user: bandwidth: 200 realm: n���d�1�gQ�,<���� with nonce
After appears
1309 2020-10-15 07:26:57,690741 10.49.66.61 10.49.64.195 STUN 173 Allocate Error Response error-code: 436 (*Unknown error code*) The Username supplied in the request is not known[Malformed Packet]
whats is error code 436, why the credentials don't are recognized ?
thanks for a response
regards
Roberto
hi jeff,
i install standard SFB with an edge server. i have some questions. my internal domain is different with my top level domain name.
i set my primary dns suffix to internal domain name and access edge service with top level domain. is it correct or not?
such this: edge server fqdn name: lynkedge.behp.local access: lynk.behphar.com
on edge server the internal nic and external nic have same ip subnet is it true? i read somewhere they must be in different subnets
The internal and external NICs must be on different subnets. The internal FQDN name can be anything and it usually is in an internal-only namespace, if applicable in your environment. The external hostnames must use the SIP domain name.
I use similar setup in our production.
Access Edge:5061
Web: 444
A/V:443
Remote login is getting failed with port 5061, i have to change it to Access Edge:443
Please advise if i can define the topology as below.
Access Edge:443
Web: 444
A/V:442
You really need to use standard ports (80/443) or many remote clients will not be able to connect to your Edge Server. Those other non-standard ports may not be reachable from many external clients across firewalls and proxies.
God bless you