I little used portion of the OCS installation wizard is the ability to delegate some access rights to specific user accounts so that remote or junior administrators can deploy OCS components on server in a environment without actually needed to have full administrative rights.
Launch the OCS 2007 Deployment Wizard and (depending on if it’s Standard or Enterprise Edition) select the Deploy Standard Edition Server or either of the Deploy Pools options. Select Prepare Active Directory and Step 7 will be Delegate Setup and Administration.
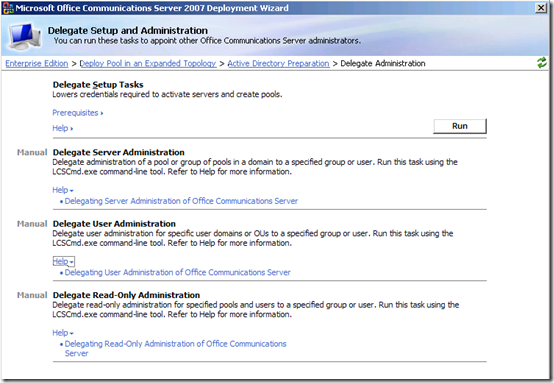
From this wizard only the Delegate Setup Tasks can be performed, as illustrated by the screenshot below. These administrative tasks must all be performed manually and directions for each scenario are included, as well as links to the deployment guides. The OCS 2007 Active Directory Guide covers these steps starting on page 17.
Delegate Setup Tasks
The wizard runs through the following screens as asked for a couple pieces of information:
- Authorize Group
- Select which domain in the forest that rights will be delegated to.
- Create a new Universal Security Group called RTCSetupDelegate in the domain and enter the name here.
- Location of Computer Objects for Deployment
- Enter the fully distinguished name of the OU where the server’s computer objects are stored (or will be stored) on which the OCS components will be deployed. I created a child-OU called "OCS Servers" in my normal "Servers" OU as to limit the scope of objects that the delegated accounts could deploy OCS to. Ideally you would pre-deploy the computer objects in this location.
- Service Account
- Unless custom account names were chosen during installation then the SIP and Component Service accounts are RTCService and RTCComponentService.
The deployment log details all of the checks and changes that are applied by the wizard.
The new RTCSetupDelegate group is added as a member to the existing RTCUniversalGLobalReadOnlyGroup and RTCUniversalGlobalWriteGroup groups.
The following permissions were assigned to the RTCSetupDelegate group on the OU specified in the wizard:
| Permission | Apply To | Object Permission | Properties Permissions |
| Special | Special | Allow List Contents, Read/Write All Properties Delete Subtree, Read/Modify Permission Create/Delete All Child Objects Create/Delete All msRTCSIP-MCU Objects Create/Delete All msRTCSIP-Mediation Objects Create/Delete All msRTCSIP-Server Objects Create/Delete All msRTCSIP-WebComponents Objects |
Read/Write All Properties |
| Special | msRTCSIP-Server objects | Read/Write All Properties, Delete Subtree | Read/Write All Properties |
| Special | msRTCSIP-MCU objects | Read/Write All Properties, Delete Subtree | Read/Write All Properties |
| Special | msRTCSIP-WebComponents objects | Read/Write All Properties, Delete Subtree | Read/Write All Properties |
| Special | msRTCSIP-Mediation Server objects | Read/Write All Properties, Delete Subtree | Read/Write All Properties |
| Read Public Information | Computer objects | Read Public Information | |
| Read DNS Host Name Attributes | Computer objects | Read DNS Host Name Attributes | |
| Special | This object only | List Contents, Read All Properties, Read Permissions | Read All Properties |
The Deployment Log that is present after the process completes will outline every little detail of all checks performed and changes made. In fact, more than you probably ever need to know 🙂
Delegate Administration
The remaining scenarios allow administrators to grant access to other user and group objects so that these accounts or members can perform administrative tasks against OCS servers and users without simply being put into the Domain Admins group. Even Read-Only administrative rights can be delegated out quite simply.
Each of these tasks are completed by using the lcscmd.exe command as documented in the AD Guide.