There are a handful of tools and scripted solutions floating around for resolving SIDs to user accounts and the reverse, but here’s a handy way to do this by simply using Active Directory Users and Computers.
The first time you perform this for a domain it will be necessary to identify the RID and GUID portions of the domain’s SID, so that you can create an LDAP Query, and then any future lookups will only require some quick match to convert the GUID portion into a format suitable for searching AD with. (The Additional Account Info tab makes it easy to double-check your work, so grab it from the Account Lockout and Management Tools page on Microsoft Download if you aren’t already using it; it’s a great plug-in for ADUC.)
The scenario is that we have a SID for an unknown user account in the domain and we need to figure out what user account it belongs to. For example, maybe there is a large Recycle Bin (which displays the file owner’s SID) sitting on a terminal server with hundreds of local profiles and we need to know what user it belongs to. Whatever the reason, having a Saved Query in ADUC is handy when you need to perform quick LDAP searches on AD.
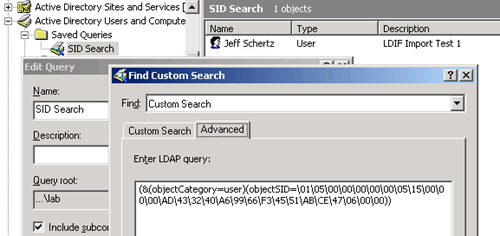
So go ahead and create a new query and name it SID Search. Set the Find field to Custom Search and copy/paste this string into the Advanced tab:
(&(objectCategory=user)(objectSID=NULL))
This search will clearly not return anything, as NULL is just a place holder for the time being. What needs to go in it’s place is an objectSid value in a particular format. Let’s go ahead and pull the value from my own user account in my test lab to test this search query.
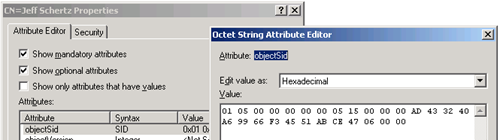
Using ADSI Edit I’ll copy the objectSid value as displayed in hexadecimal format:
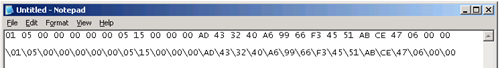
And then paste it into a plain text file, replacing all the spaces with \ characters:
This \-separated string should replace the NULL in our search query. Hit refresh on the SID Search query and the results should appear:
Now we have a quick search that can be used by replacing the value of the objectSID in the query with the SID for an unknown user and ADUC will quickly return the matching user account (if it has not been deleted from AD.)
Where things get a little tricky is a SID is typically represented like this: S-1-5-21-1077035949-4083587494-3467333957-1607. For the mechanics of converting a SID in this format into hexadecimal for the purposes of using our query, take a look at one of my old blog entries which explains the math behind this process. I’ll quickly run through the steps here as once your understand the process it’s very easy to perform routinely.
- Record the unknown User’s SID: S-1-5-21-1077035949-4083587494-3467333957-1138
- Compare to another account in the same domain to isolate and verify the GUID portion (typically the value after the last hyphen): 1138
- Use calc.exe in Scientific Mode to convert 1140 decimal into hexadecimal: 472
- Rewrite that value in 8 digit format: 00000472
- Separate the value in pairs of digits: 00 00 04 72
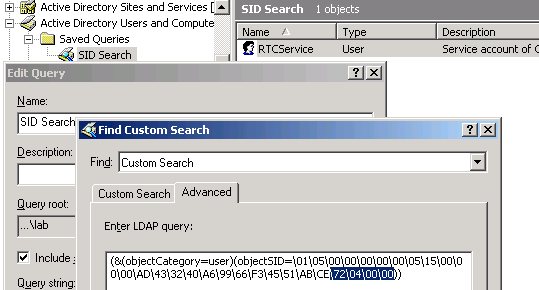
- Re-order the pairs in reverse: 72 04 00 00
- Replace the last 4 hexadecimal values in the query string: \47\06\00\00 becomes \72\04\00\00
So I’ve discovered that the domain user account for S-1-5-21-1077035949-4083587494-3467333957-1138 is actually RTCService. This simple query is just one example; you could change the query with (objectCategory=*) to broaden the search scope to include security groups and other non-user account objects if desired.
More LDAP Queries
In fact, here are some other custom queries I have made out of necessity which have proven to be quite handy. Once you understand how a specific AD attribute is used it’s quite easy to create simple queries to identify subsets of objects for pretty much anything you can think of.
- Displays any user accounts with Outlook Web Access disabled
(&(objectCategory=user)(protocolSettings=*HTTP*0*))
- Searches for any mailbox-enabled account which are not using the Exchange Storage Quota defaults
((mailNickname=*)(mDBUseDefaults=FALSE))
- Shows any user accounts with a Receiving message size limit set
(&(legacyExchangeDN=*)(mailNickname=*)(objectCategory=person)(objectClass=user)(delivContLength=*))
- Shows any user accounts with a Sending message size limit set
(&(legacyExchangeDN=*)(mailNickname=*)(objectCategory=person)(objectClass=user)(submissionContlength=*))
- Searches for X500 addresses that start with this specific org and ou
(&(objectCategory=group)(proxyAddresses=X500:/o=Schertz/ou=Lab*))
- Looks for mail-enabled public folders which are visible in the Global Address List
(&(objectCategory=publicFolder)(msExchHideFromAddressLists=FALSE))(& (displayName=*))
This is really helpful – thanks
Trank you very much!