This article covers various methods for identifying the Directory ID and Object ID values for tenants and user accounts in Microsoft’s Office 365 environment. These Universally Unique Identifiers (UUID) are assigned to the overall directory and each user individual account that exists in Azure Active Directory (AAD), whether the account was created in the cloud or was initially created on an Active Directory (AD) on-premises instance and was then synchronized to the cloud.
The tenant identifier is referenced with different names depending on where the value is being retrieved from and it uses the same 32-character, dash-separated, hexadecimal format as the individual Object IDs use. Also with the user accounts the term “Object ID” can refer to either/both the AzureAD account’s actual numeric identifier or the account’s UserPrincipalName (UPN) value. So, for example, a valid Object ID for a user account could be ‘jeff@jdskype.net‘ and ‘e0d3ad3d-0000-1111-2222-3c5f5c52ab9b‘. In essence a query using the Object ID (UPN) can be issued to return the Object ID (Numeric).
In the event that a numeric identifier is be needed this article can be used as a quick reference for querying for the different values in a multiple ways. Additionally the latter half of this article shows how to install either or both of the prerequisite PowerShell modules for managing Azure AD.
Using the Admin Center
The easiest option is to simply use the GUI-based admin centers available to Office 365 tenant administrators, but for repeated or bulk tasks PowerShell is usually the preferred route. The Office 365 Admin Center includes an Azure AD specific administration console which can be used to browse for a specific user account and locate the Object ID value.
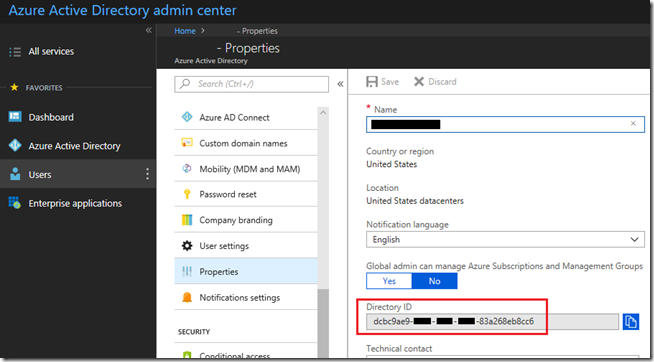
Tenant (Directory ID)
- Open the Office 365 Admin Portal and sign-in with an account in the desired tenant which has been delegated the appropriate administrative rights.
- In the main menu on the left expand the Admin Centers section at the bottom and then click on the Azure Active Directory option to launch the console in a new browser window.
- In the Azure Active Directory admin center menu select Azure Active Directory and then navigate to Manage > Properties.
- The Directory ID field will be displayed as shown in the following screenshot.
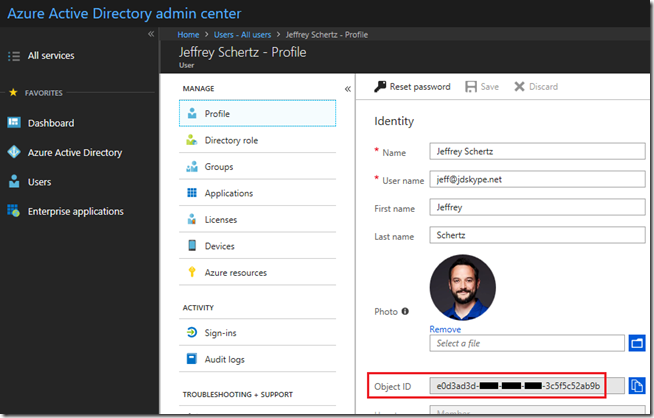
User (Object ID)
- Open the Office 365 Admin Portal and sign-in with an account in the desired tenant which has been delegated the appropriate administrative rights.
- In the main menu on the left expand the Admin Centers section at the bottom and then click on the Azure Active Directory option to launch the console in a new browser window.
- In the Azure Active Directory admin center menu select Users.
- Browse to or search for the desired user and then click on the account name to view the user account’s Profile information.
- The Object ID field will be displayed in the Identity section as shown in the following screenshot.
Using PowerShell Modules
For quick reference purposes this portion is written out-of-order. If the proper PowerShell modules have already been configured on a workstation or server then the following cmdlet should work as shown. But if the required first-time setup for using PowerShell with Office 365 has not yet been completed then skip down to the Configuring PowerShell Modules section and then once complete return to the cmdlets shown here.
AzureAD
The newer Get-AzureAD cmdlet can be used to locate teh Object ID value and is the recommended cmdlet set to use by Microsoft.
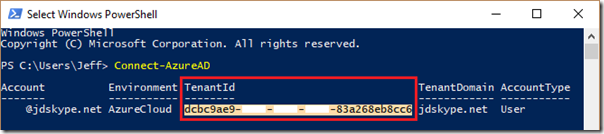
- Launch Windows PowerShell and issue the Connect-AzureAD cmdlet. A separate authentication window will appear.
Connect-AzureAD
- Enter the credentials of an administrative account for the desired Office 365 tenant. If authentication is successful then Tenant ID will automatically be displayed.
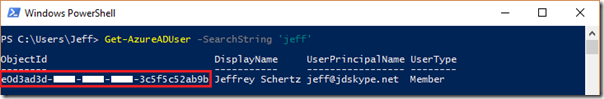
- Enter the following Get-AzureADUser cmdlet to locate the Object ID for a specific user account by searching against the account name.
Get-AzureADUser -SearchString ‘jeff’
MSOnline
If preferred the Get-MsolUser cmdlet can also be used to locate the Object ID value.
- Launch Windows PowerShell and issue the Connect-MsolService cmdlet. A separate authentication window will appear.
Connect-MsolService
- Enter the credentials of an administrative account for the desired Office 365 tenant. If authentication is successful then some account and tenant information will be displayed.
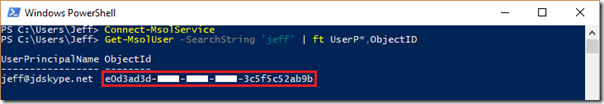
- Enter the following Get-MsolUser cmdlet to locate the Object ID for a specific user account by searching against the account name.
Get-MsolUser -SearchString ‘jeff’ | ft UserP*,ObjectID
Installing PowerShell Modules
In order to run the commands shown above the proper PowerShell module(s) must first be installed or imported. This section covers the one-time setup for both the older and newer management modules. These two options are provided via two different PowerShell modules available today for managing Azure AD objects: MSOnline and AzureAD. These separate PowerShell modules must be installed or imported on a Windows workstation but the processes for doing so has changed over time. The newer AzureAD module is the preferred method for managing Azure objects.
Older guidance related to using the MSOnline PowerShell cmdlets outlined having to separately install the Microsoft Online Services Sign-In Assistant and Azure AD PowerShell modules but these steps are no longer required in most cases. Firstly, all Office 365 tenants can now leverage Modern Authentication so the older sign-in assistant is not required. Secondly, the needed PowerShell modules are available in the online PowerShell Gallery and can simply be imported when PowerShell 5.0 or newer is used.
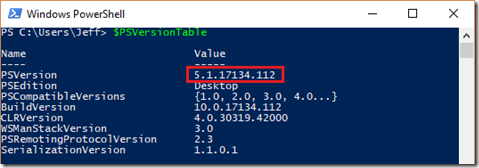
- To validate the version of PowerShell on the desired Windows system run the $PSVersionTable cmdlet in PowerShell.
$PSVersionTable
For the purposes of the remainder of this article it is assumed that Windows 10 or Windows Server 2016 is being utilized, which both include PS 5.0 or newer depending on the applied Windows Updates. Using an older version of PowerShell may require downloading and installing some modules manually.
Azure Active Directory PowerShell 2.0
As stated earlier Microsoft encourages customers to leverage the newer Azure Active Directory PowerShell module, so for any new workstation or server configuration then this is the preferred process. Just as outlined above PowerShell 5.0 or newer is required to install the needed modules as shown below. (If a PowerShell version older than 5.0 is being used then the latest version of the module can be installed manually by downloading the package from the PowerShell Gallery online.)
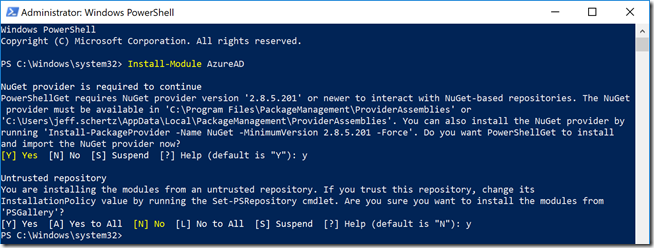
- Launch Windows PowerShell as an administrator and then run the following cmdlet to install the latest version of the AzureAD module directly from the PowerShell Gallery (a working connection to the Internet to obviously required for this step to successfully complete).
Install-Module AzureAD
If this is the first time installing PowerShell modules from the PowerShell Gallery on the specific workstation or server then two additional confirmation prompts may appear. By default Windows PowerShell does not trust NuGet galleries, nor the specific PSGallery. To configure this trust manually the steps on this Microsoft article may be followed beforehand, but are not necessary as the trust can be overridden by responding to the following prompts during the package installation.
- If the message “NuGet provider is required to continue” appears then enter “Y” to allow PowerShell to install the NuGet provider package.
- If the message “untrusted repository” appears then enter “Y” to also trust the PSGallery package.
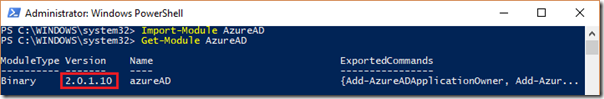
To validate that the installation was successful and to check on the version number of the installed module run the following two cmdlets in the same PowerShell window. (Note that running the Get-Module cmdlet will not return any information without first running the Import-Module cmdlet.)
Import-Module AzureAD
Get-Module AzureAD
At this point a connection can be established to Office 365 via the AzureAD module to retrieve the Object ID as shown in the previous section.
MSOnline PowerShell 1.0
This approach leverages the older, but still available, MSOnline PowerShell module for Azure Active Directory management. In order to utilize this command set the module must first be installed on a Windows workstation if it has not already been. While this module does include some options which are not currently available in the newer AzureAD module the Object ID can be queried in either as shown above.
But if none of this has been setup then it’s recommended to simply leverage the newer AzureAD module shown in the previous section.
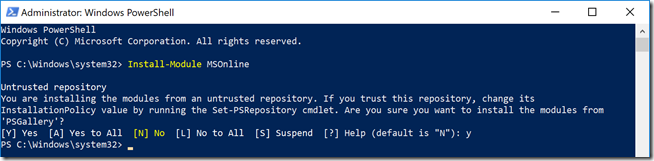
- Launch Windows PowerShell as an administrator and then run the following cmdlet to install the latest version of the MSOnline module directly from the PowerShell Gallery (a working connection to the Internet to obviously required for this step to successfully complete).
Install-Module MSOnline
If this is the first time installing PowerShell modules from the PowerShell Gallery on the specific workstation or server then two additional confirmation prompts may appear. By default Windows PowerShell does not trust NuGet galleries, nor the specific PSGallery. To configure this trust manually the steps on this Microsoft article may be followed beforehand, but are not necessary as the trust can be overridden by responding to the following prompts during the package installation.
- If the message “NuGet provider is required to continue” appears then enter “Y” to allow PowerShell to install the NuGet provider package.
- If the message “untrusted repository” appears then enter “Y” to also trust the PSGallery package.
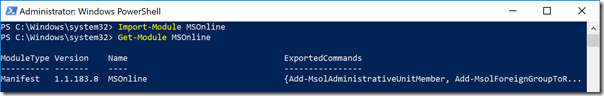
To validate that the installation was successful and to check on the version number of the installed module run the following two cmdlets in the same PowerShell window. (Note that running the Get-Module cmdlet will not return any information without first running the Import-Module cmdlet.)
Import-Module MSOnline
Get-Module MSOnline
At this point a connection can be established to Office 365 via the MSOnline module to retrieve the Object ID as shown in the previous section.
Hi Jeff!
Could you please unveil is it possible to obtain Object ID of Active Directory Group User, currently logged in Azure SQL database, from the database level (in TSQL) ?
Best regards,
Alex R.
I don’t know if you can query SQL directly for that value and if so, what it would be stored under.
Hello Jeff,
Thanks for this article. I am new to Azure AD and working on integrating Azure AD with other application. What I observed is, when the Azure AD is synced with on premises AD, Azure AD User Object Id is getting changed every time there is any update for the user record from on premises AD. Have you seen such behavior before? Should UserPrincipalName be used as unique Id in this case? Is there a scenario under which UserPrincipalName could change for the user account?
I’m not sure on the ID behavior, but the UPN should not change on the account regardless of its synchronization status.
in one of the subscriptions i manage, someone deleted a virtual machine. the event was initiated by an account with a numeric id. how can i find the users alias from this object id?
Our on-premise .NET desktop application (back-end is SQL Server 2017) tracks which users have created and made changes to records, identifying the user by calling System.Security.Principal.WindowsIdentity.GetCurrent.Name, which returns a value with the format DOMAIN-NAME\username. If we were to move everything up to the cloud, to Azure, the SQL database as well as the desktops, so that the users would be running the .NET client desktop program in Microsoft Azure DAAS, would we be able to have continuity in terms of these user identities? Could our desktop program still call System.Security.Principal.WindowsIdentity.GetCurrent.Name and get back OURDOMAIN\jdoe?